Researchers quantify the promise and limits of new crypto hacking algorithms.

Researchers quantify the promise and limits of new crypto hacking algorithms.
It may be old news now, but hackers are still using news of the royal baby’s birth to entice people into clicking on malicious links, according to researchers at Trend Micro.

Windows’ share of the tablet market grew slightly in the second quarter, as shipments also ticked up in the face of a slow-down by tablets overall, researcher IDC said today.

The vulnerability was reported Thursday to Oracle along with proof-of-concept (PoC) exploit code.
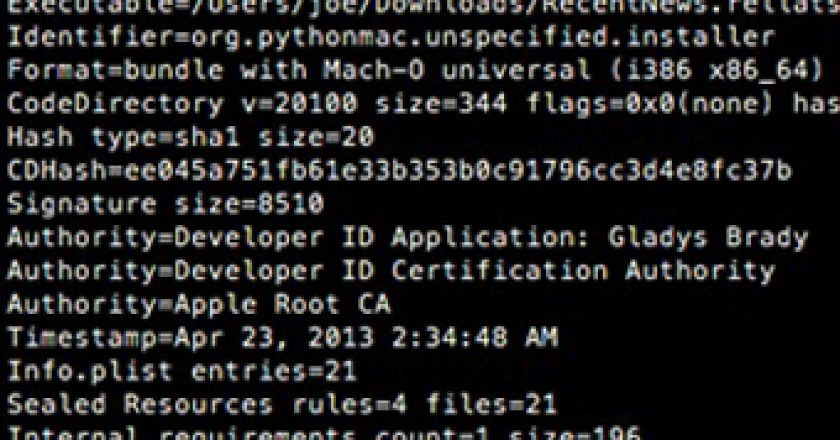
Researchers at F-Secure have discovered malware targeting OS X, which leverages a technique called right-to-left override (RLO) in order to spoof its malicious nature.

A new version of a file-infecting malware program that’s being distributed through drive-by download attacks is also capable of stealing FTP (File Transfer Protocol) credentials.
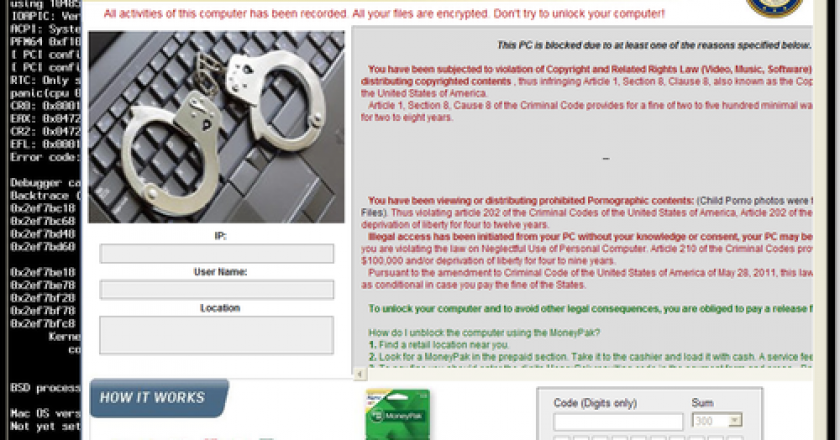
A persistent, widespread malware campaign that utilises compromised Apache servers is locking users’ computers and demanding a fee of $300 to free their data.

Right before bedtime, bright lights are the enemy, inhibiting the production of melatonin, which helps you fall (and stay) asleep.

With the previously $40,000 Carberp Trojan’s source code now freely available, experts expect exceptionally destructive variants of the malware to flow onto the Internet.

SAP has significantly improved the security of its products over the past few years but many of its customers are negligent with their deployments, which exposes them to potential attacks that could cripple their businesses, according to security researchers.
GET TAHAWULTECH.COM IN YOUR INBOX