Organisations with Real-Time Data Streams See Higher Revenues and Happier Customers, Confluent Report Finds.
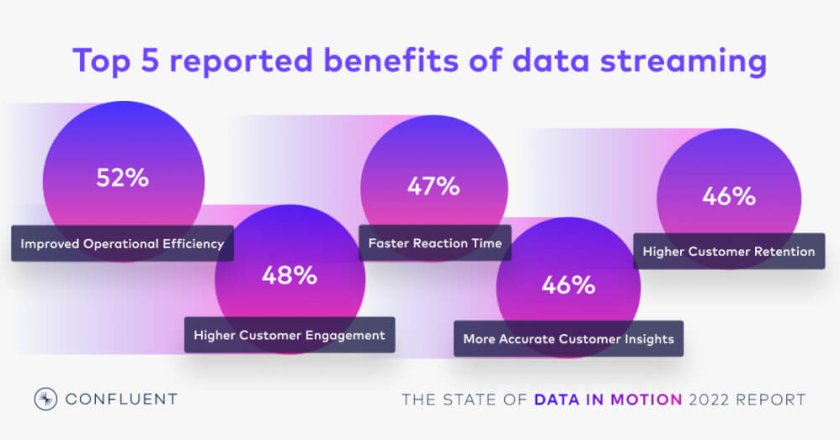


Organisations with Real-Time Data Streams See Higher Revenues and Happier Customers, Confluent Report Finds.

Cybereason Announces Inaugural Report from the Cyber Defenders Council on New Model for Cyber Deterrence.

Cybercriminals Laundered $8.6 billion Worth of Cryptocurrency in 2021, Reveals Chainalysis Report.

Kaspersky’s new Women in Tech report – women in tech face lockdown barriers to career progression.

Tim Taylor QC, Managing Partner at King & Wood Mallesons Dubai, has penned a forensically in-depth op-ed on the rivalry …

The Majority of UAE Professionals Want Virtual Working Environments To Remain In Post-Pandemic Era. New BCG and Bayt.com report also identifies other worker preferences and expectations concerning full-time office returns, career progression drivers, and personal values.

CNME Editor Mark Forker managed to secure an exclusive interview with Wissam Khoury, Head of International, at Finastra, to learn …

Futurum Research, sponsored by SAS, the leader in analytics, shared new research called “Experience 2030: The Future of Customer Experience” …

A survey by Bloomberg has found that prominent thought-leaders in the Middle East, believe that China and India has now …

A comprehensive report from IT leader Veeam Software, has shown that poor data management is costing businesses millions every year.
GET TAHAWULTECH.COM IN YOUR INBOX