However, Dubai is the most expensive city to surf the Internet, according to a Deustche Bank report.



However, Dubai is the most expensive city to surf the Internet, according to a Deustche Bank report.

According to a study by IT management solutions provider, CA Technologies, 47 percent of senior leaders agree that the role of …
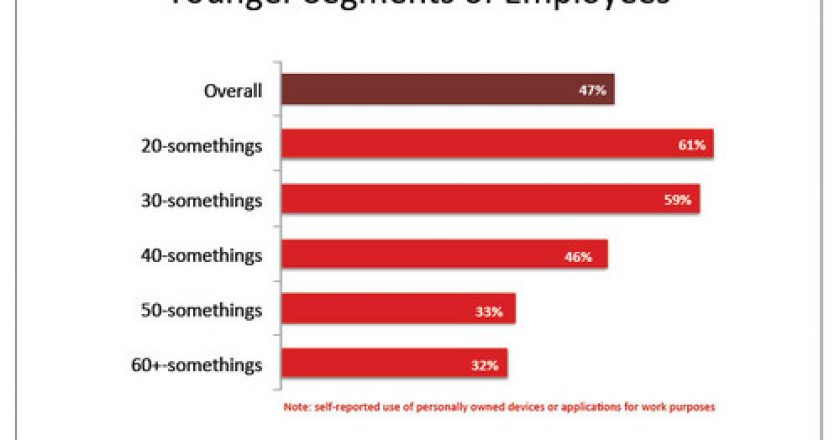
CIOs who think they can abandon BYOD risk upsetting an important and growing constituency of their workforce: millennials, also known as Generation Y.
Fragmentation has been both a blessing and a curse for Android since the beginning, and a new report says that’s not changing any time soon.

A Home Affairs Select Committee has stated that the UK is losing the war on online criminal activity and that the government is too complacent in targeting cyber criminals.

Using text analytics technology to analyse call-centre transcripts and customer surveys, emails and tweets can improve customer service.

New research has shown that the vast majority of businesses are exposing sensitive corporate data to cyber-criminals by failing to implement effective BYOD strategies.

A new report from the SANS Institute and RSA on help desk security and privacy finds help desk workers are the easiest victims for a determined social engineering criminal.
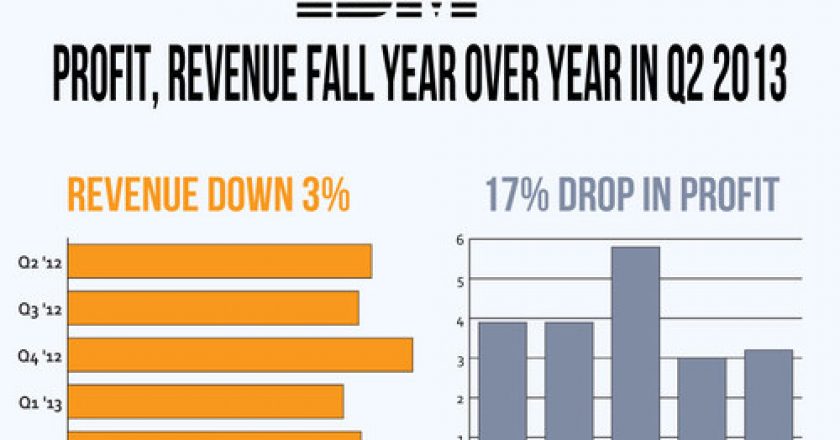
A rebound for IBM failed to materialise in the second quarter, as profit and sales declined along with a slump in revenue from hardware and services.

The US may be the global centre of the IT universe, but India will exceed the US in the number of software developers by 2017, a new report notes.
GET TAHAWULTECH.COM IN YOUR INBOX