*This article was originally published on SAS blog by Federica Citterio Augusta Zhang and Jacek Dobrowolski also contributed to this article. …



*This article was originally published on SAS blog by Federica Citterio Augusta Zhang and Jacek Dobrowolski also contributed to this article. …

Facebook and Microsoft are winning plaudits from security researchers for launching an initiative to offer bounties to bug hunters who discover and report vulnerabilities in widely used products.
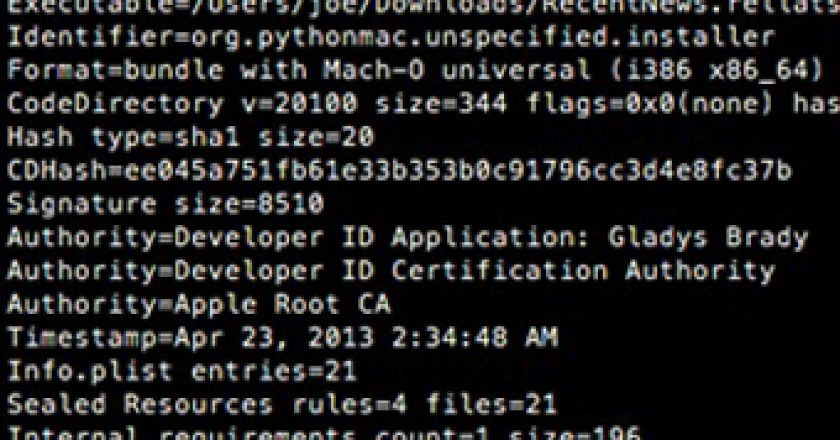
Researchers at F-Secure have discovered malware targeting OS X, which leverages a technique called right-to-left override (RLO) in order to spoof its malicious nature.
Google is hoping to appease developers that want better portability for their hosted apps by working with Red Hat on running App Engine in private clouds.
After two years of beta testing, the Red Hat OpenShift Online platform as a service (PaaS) has been pressed into commercial use, …
GET TAHAWULTECH.COM IN YOUR INBOX