emt Distribution announces Partnership with ondeso for Middle East and Africa to help Organisations with Operational Technology & Installed Base Management.


emt Distribution announces Partnership with ondeso for Middle East and Africa to help Organisations with Operational Technology & Installed Base Management.
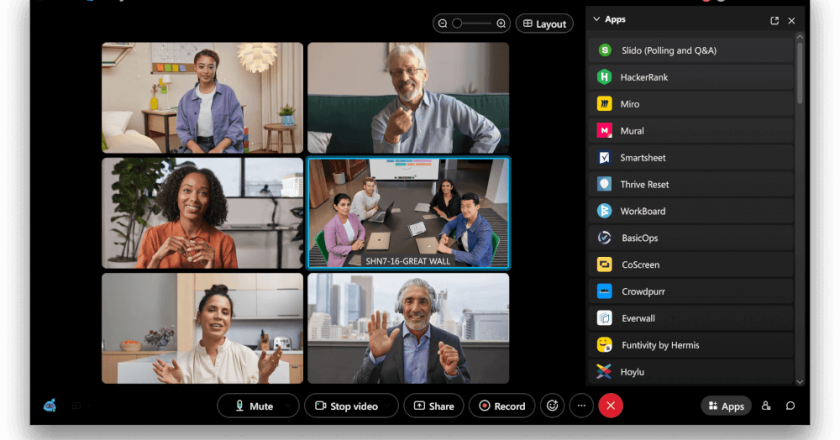
New Webex by Cisco Innovations Address Challenges of Hybrid Work for Organisations of All Sizes.

Nitya Ravi of CPI speaks to Mr. Ali Bahlooq, General Manager of Esharah Etisalat Security Solutions about the innovative solutions they offer to the organisations.

Nitya Ravi speaks to Dr. Cherif Sleiman of Safe Security who explains the mistake organisations are making when it comes to Enterprise-wide security breaches.

As we’ve seen over the past 18 months, video communications have tremendously benefited individuals, families, organisations, and governments. Video meetings made it possible for people to connect and collaborate even as they were miles apart. Moreover, many organisations came to realise how video communications improve productivity and work-life balance.

Document Scanners Backed by Comprehensive Services Improve ROI and Allow Organisations to Focus on Business Priorities.

Despite the significant Java security improvements made by Oracle during the past six months, Java vulnerabilities continue to represent a major security risk for organisations.

Swiss structured cabling specialist R&M has warned Middle East organisations against premature investments as long as standards are not defined and components are not fully developed.

US cloud providers could miss out on billions of euros of business from European customers due to data privacy fears around the Prism surveillance programme, the European Commission has claimed.

Companies and organisations should ensure that they have a full 360-degreee view of their data, says AccessData’s Paul Wright.
GET TAHAWULTECH.COM IN YOUR INBOX