A steady stream of questionable applications is flowing daily into Google’s Play store for Android devices, according to security vendor Symantec.
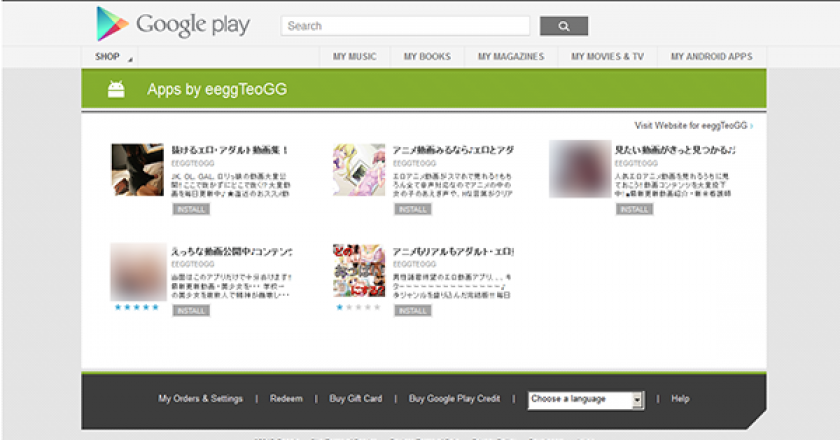


A steady stream of questionable applications is flowing daily into Google’s Play store for Android devices, according to security vendor Symantec.

Malware removed from forty percent of computers in those botnets, according to the vendor.

With the major developers of banking malware laying low, a new crook on the block has emerged gunning to be top dog in the market.
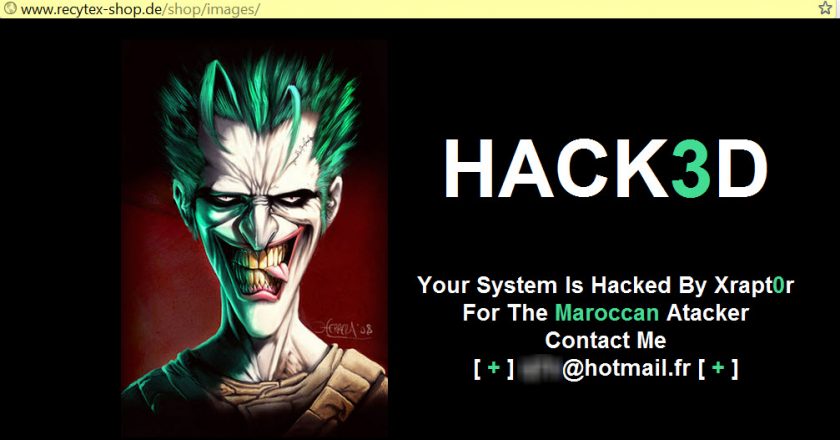
Cyber-criminals are compromising websites at hosting companies at an ever-furious rate.

An increasing number of Android phones are infected with mobile malware programs that are able to turn the handsets into spying devices.

The impact of hacked SIM cards, one of the few stalwarts in the high-tech industry that has not seen a serious exploit, could be monumental.

Millions of mobile phones may be vulnerable to spying due to the use of outdated, 1970s-era cryptography, according to new research due to be presented at the Black Hat security conference.
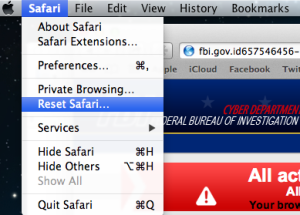
Ransom attackers have finally made the jump from Windows to the Mac with news of a stunningly simple hack that tries to trick browser users into paying a $300 (£200) fine using a simple JavaScript routine.

New research has shown that the vast majority of businesses are exposing sensitive corporate data to cyber-criminals by failing to implement effective BYOD strategies.
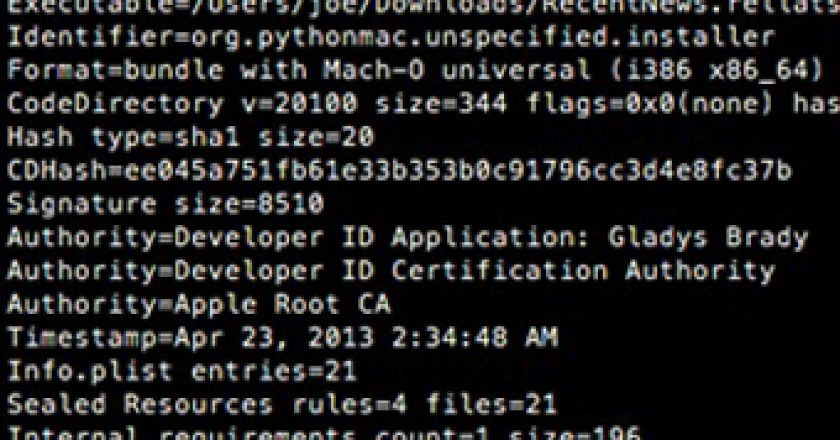
Researchers at F-Secure have discovered malware targeting OS X, which leverages a technique called right-to-left override (RLO) in order to spoof its malicious nature.
GET TAHAWULTECH.COM IN YOUR INBOX