Global SOHO, SMB networking products and wireless LAN solutions provider TP-Link Technologies has announced a plan that will see it …



Global SOHO, SMB networking products and wireless LAN solutions provider TP-Link Technologies has announced a plan that will see it …

Dubai Trade is gearing up for its upcoming 10th E-Services Excellence Award (ESEA) by featuring four new categories to recognise …

Enterprise all-flash solutions provider Pure Storage has announced its participation at GITEX Technology Week, which will be held from 8th to 12th October at the Dubai World Trade Center (DWTC).

Omantel has signed a Memorandum of Understanding with the Ministry of Environment and Climate Affairs (MECA) for Information and Communication Technology (ICT) solutions.

End-user spending for the worldwide virtual personal assistant (VPA)-enabled wireless speaker market is forecast to reach $3.52 billion by 2021, up from $0.72 billion in 2016, according to Gartner.

Arun Khehar, senior vice president of applications, Oracle ECEMEA, gives his take on why blockchain has the potential to revolutionise various industries and provide enhanced transparency to finance.
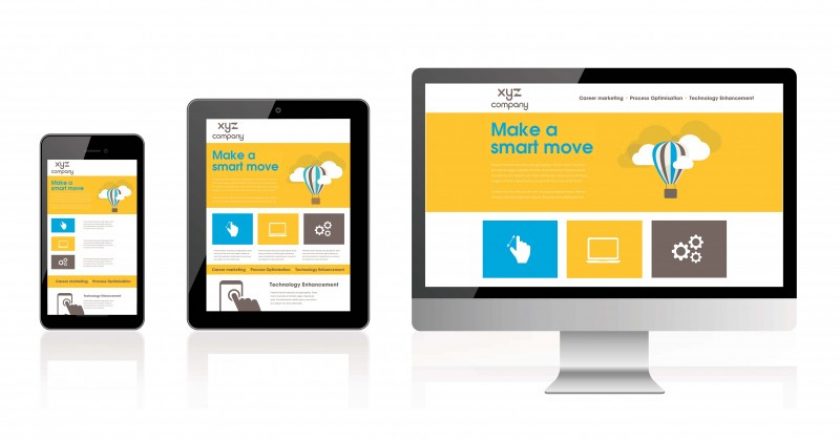
Cazar, developer of Sniperhire, an e-recruitment system in the GCC, has chosen Microsoft Azure to enhance its solution and future-proof its already-innovative software.

Fortinet has announced the findings of its latest Global Threat Landscape Report, which revealed that poor cybersecurity hygiene and risky application usage enables destructive worm-like attacks to take advantage of hot exploits at record speed.

Sony announces its smart speaker, the LF-S50G, which comes powered by Google Assistant at IFA 2017.

The photo-sharing company said it found a bug that exposed people’s email addresses and phone numbers, which it quickly fixed.
GET TAHAWULTECH.COM IN YOUR INBOX