Report underscores that email is the most exploited threat vector, phishing remains borderless and attackers are increasingly impersonating trusted name brands.
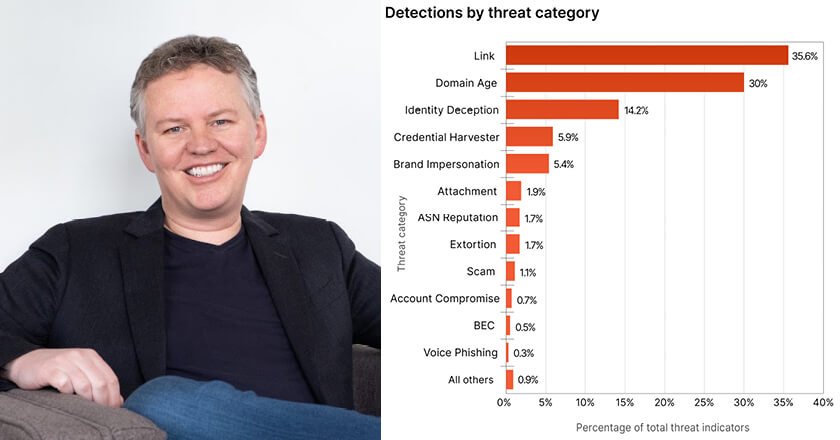

Report underscores that email is the most exploited threat vector, phishing remains borderless and attackers are increasingly impersonating trusted name brands.
GET TAHAWULTECH.COM IN YOUR INBOX