Microsoft is working to help its enterprise customers move their data, apps and operations to the cloud – specifically the hybrid cloud.


Microsoft is working to help its enterprise customers move their data, apps and operations to the cloud – specifically the hybrid cloud.

SAP and IBM share a long history dating back to the very roots of SAP, and on Monday that allegiance got a little closer with two new IBM Power Systems server configurations tailored specifically for SAP’s Hana in-memory data platform.

Fortinet today announced that the National Clearing Company of Pakistan Limited (NCCPL) has deployed FortiGate integrated network security appliances and FortiClient endpoint software at its head offices and disaster recovery site

The Networked Society is important in all aspects of life today, and especially going forth into the future. It is a starting point for innovation, socialisation and changing the way in which whole communities interact and live their lives.
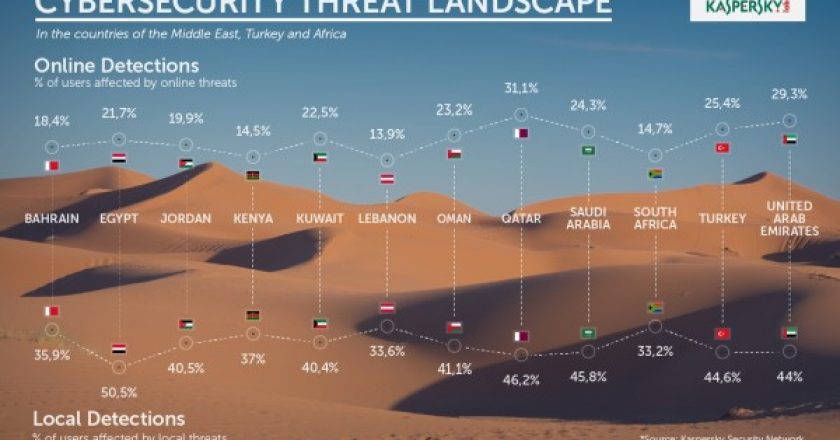
Kaspersky Lab’s Cyber Security Weekend for the Middle East, Turkey and Africa which took place April 26-29 in Lisbon, Portugal and brought together specialists from the Kaspersky team, an expert from EY, journalists and business guests.

Strapped to your wrist, the Apple Watch goes everywhere that you go. Between it and the iPhone, it’s almost possible …

As part of its expansion in the Middle East, IBM will be launching its first office in Kuwait.

Samsung Electronics regained the number one position in the smartphone market in the first quarter.

Apple achieved its second straight quarter of record results as demand for the new iPhone 6 surged and China became Apple’s second most important market after the US.

Cisco today unveiled a host of new capabilities and services that give security professionals extensive intelligence and analysis on potential compromises and solutions to protect against, respond to and recover from attacks.
GET TAHAWULTECH.COM IN YOUR INBOX