Researchers at F-Secure have discovered malware targeting OS X, which leverages a technique called right-to-left override (RLO) in order to spoof its malicious nature.

Researchers at F-Secure have discovered malware targeting OS X, which leverages a technique called right-to-left override (RLO) in order to spoof its malicious nature.

Cisco is building a router for the Internet of Everything, the company’s initiative to connect the billions of devices – or 99 percent of the world – that it claims isn’t already connected.

The first tools for injecting legitimate Android apps with open-source software that allows an attacker to control an infected smartphone remotely have been found in the criminal underground.
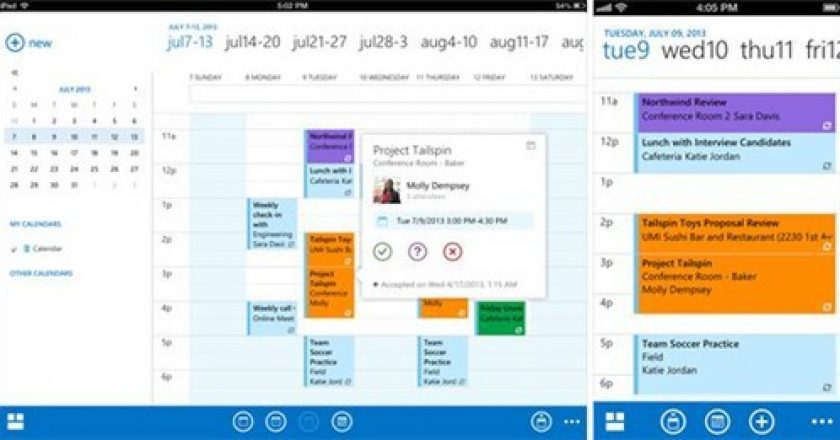
In an odd bit of doublespeak, Microsoft has released a version of its Outlook Web App (OWA) as a native application for the Apple iPhone and iPad.

A new version of a file-infecting malware program that’s being distributed through drive-by download attacks is also capable of stealing FTP (File Transfer Protocol) credentials.

Oracle is introducing a new generation of its Exalytics appliance for high-speed data analysis that comes with a slightly higher price tag but major increases in memory and storage capacity.

Symantec has discovered a bizarre ransom Trojan that eschews the usual demand for payment in favour of asking its victims to fill in an online survey to get an unlock code.

With major parts of the US under an intense heat wave, opting for less cooling may seem like a bad idea. But it isn’t.

Microsoft Chairman Bill Gates on Monday briefly took attendees at a company-hosted research conference back decades to the failure of Microsoft Bob and the loathed ‘Clippy’.

The Chinese cyber-spies behind the widely publicised espionage campaign against The New York Times have added Dropbox and WordPress to their bag of spear-phishing tricks.
GET TAHAWULTECH.COM IN YOUR INBOX