The Edward Snowden saga continues to serve up valuable lessons on the dangers posed to enterprise data by insiders with privileged access to systems and networks. The latest lesson involves the risks of allowing password sharing among employees.


The Edward Snowden saga continues to serve up valuable lessons on the dangers posed to enterprise data by insiders with privileged access to systems and networks. The latest lesson involves the risks of allowing password sharing among employees.

Despite the frothy headlines stirred by Twitter’s initial public offering, tech is not in a bubble of the sort that arose before the 2000 dot-com crash.

The engineer who oversaw development of Apple’s Siri technology is now at Samsung building an online service to link together the “Internet of things.”

Microsoft has shortened its list of CEO candidates to a minimum of eight, including five outsiders and three current executives, according to the Reuters news service.

The battle between Apple and Samsung over smartphone design returns to a Silicon Valley courtroom next week as the companies fight over how much Samsung should pay for infringement of five Apple patents in 13 of its smartphones.
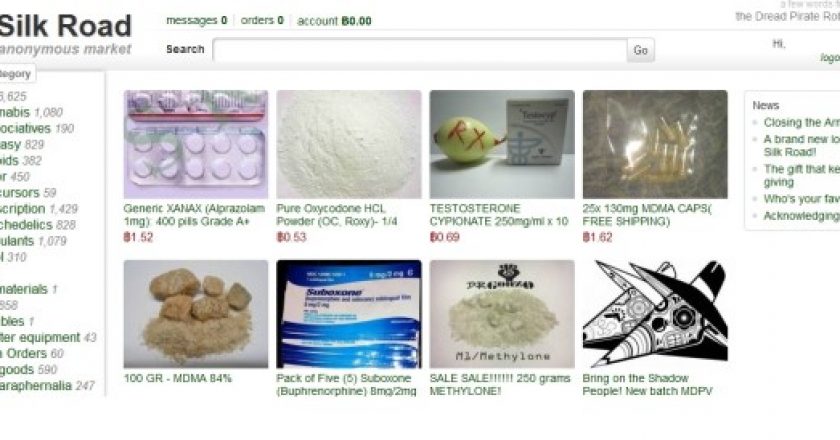
The Silk Road online marketplace has resurfaced about a month after U.S. officials shut down the website that was only accessible through the Tor anonymity service.

Google’s secret proposals leaked as dismay over EU antitrust inquiry grows

Spear phishing is one of the most effective ways to break into a corporate network – and recent studies show that employees can be easily tricked on social media to provide the information needed to launch attacks.

Microsoft today said that attackers are exploiting a critical and unpatched vulnerability in Office 2007 using malformed documents to hijack Windows PCs, and that Office 2003 and Office 2010 are also vulnerable.

Apple have revealed the amount of user information that governments have requested from the California giant, as it sought to set itself apart from Silicon Valley competitors whose businesses are built on amassing personal data.
GET TAHAWULTECH.COM IN YOUR INBOX