Researchers have demonstrated that microphones and speakers built into laptops can be used to covertly transmit and receive data through inaudible audio signals.


Researchers have demonstrated that microphones and speakers built into laptops can be used to covertly transmit and receive data through inaudible audio signals.
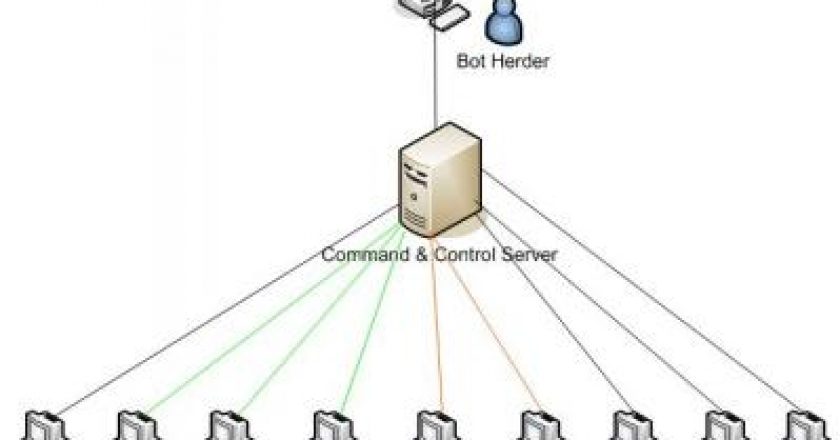
Two million logins and passwords from services such as Facebook, Google and Twitter have been found on a Netherlands-based server, part of a large botnet using controller software nicknamed “Pony.”

The Microsoft Desktop Optimization Pack (MDOP) suite of IT management tools has been updated with support for Windows 8.1 device and application management and Office 2013 virtualisation.
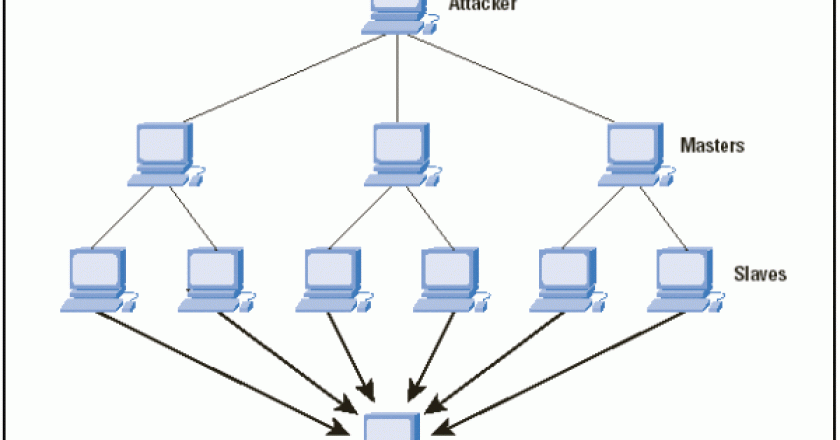
A man from Wisconsin was sentenced for participating in a DDoS (distributed denial-of-service) attack by hacker group Anonymous on a Kansas company.

After running the service in preview mode for over a year, Google is making its IaaS (infrastructure-as-a-service) Google Compute Engine (GCE) available as a full-fledged commercial service.
Apple has acquired Topsy, a social media analytics company that focuses on a range of data from Twitter, according to a recent Wall Street Journal report.

The European Central Bank (ECB) has warned that current smartphone operating systems represent a security risk as consumers adopt mobile payments.

Nokia has started shipping two new low-end touch-screen phones running its own Asha software platform. It hopes they will allow it to compete more effectively with cheap Android-based products.

Attackers are exploiting a new and unpatched vulnerability in Windows XP and Windows Server 2003 that allows them to execute code with higher privileges than they have access to.

IT departments are “significantly underestimating” the budgets allocated to technology in others parts of the organisation, as more business leaders bypass the CIO and IT staff to execute their own projects, according to research.
GET TAHAWULTECH.COM IN YOUR INBOX