The impact of hacked SIM cards, one of the few stalwarts in the high-tech industry that has not seen a serious exploit, could be monumental.


The impact of hacked SIM cards, one of the few stalwarts in the high-tech industry that has not seen a serious exploit, could be monumental.

The vulnerability was reported Thursday to Oracle along with proof-of-concept (PoC) exploit code.

A new version of a file-infecting malware program that’s being distributed through drive-by download attacks is also capable of stealing FTP (File Transfer Protocol) credentials.

The Chinese cyber-spies behind the widely publicised espionage campaign against The New York Times have added Dropbox and WordPress to their bag of spear-phishing tricks.

A second vulnerability that can be exploited to modify legitimate Android apps without breaking their digital signatures has been identified and publicly documented.

A security flaw could affect 99 percent of Android devices, a researcher claims, but the reality is that most Android users have very little to worry about.
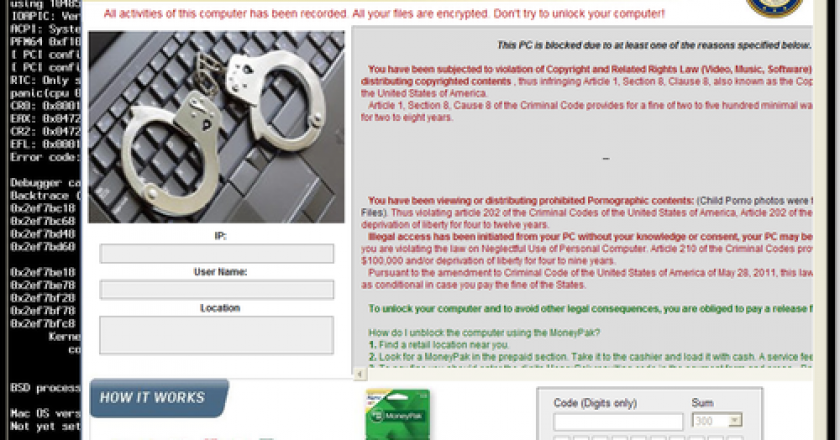
A persistent, widespread malware campaign that utilises compromised Apache servers is locking users’ computers and demanding a fee of $300 to free their data.

DDoS attackers attempted to bring down an unnamed financial services firm earlier this week using one of the largest traffic …

Another day, another critical security exploit discovered for Adobe Reader. The PDF software’s near-ubiquitous presence has made it a big, fat, …

The head of the malware analysis team at antivirus vendor Kaspersky said last week that a recently found exploit that …
GET TAHAWULTECH.COM IN YOUR INBOX