With Thanksgiving and Black Friday right round the corner, shoppers are likely to be exposed to increased risk of cybercrime. …
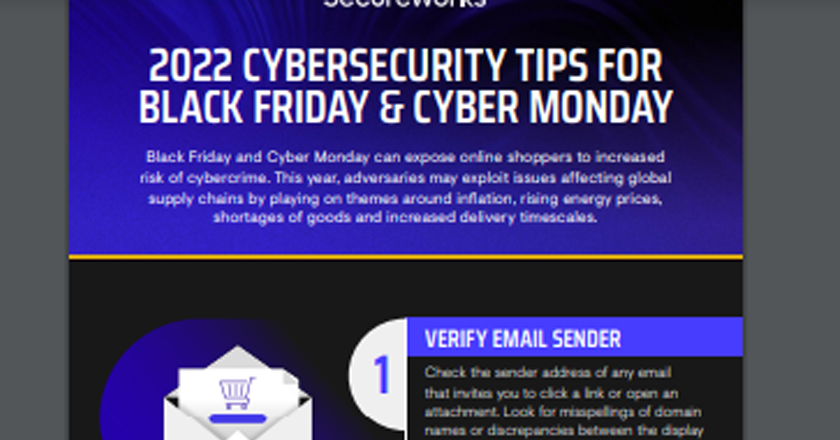


With Thanksgiving and Black Friday right round the corner, shoppers are likely to be exposed to increased risk of cybercrime. …
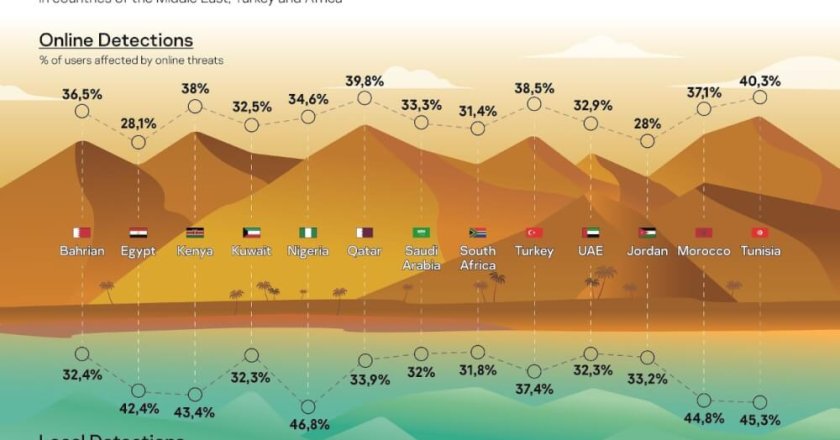
Kaspersky’s CEO Eugene Kaspersky has said that today’s hyperconnected world means that security leaders need to collaborate and completely rethink …

Richard Piasentin, Chief Strategy & Chief Marketing Officer at Accedian, tells Anita Joseph how the company is on a mission …

Universal impact of cybersecurity evident as Global Cybersecurity Forum concludes.

Ahmad Halabi, Managing Director (UAE), Resecurity, tells Anita Joseph, Editor, Security Advisor about the company’s participation at Black Hat and …

The Veeam Cloud Protection Trends Report for 2023 examines the factors that are causing IT executives to alter their strategies, …

Taj El-khayat, Managing Director – South EMEA at Vectra AI Arab Gulf nations’ reputations for technological prowess are well deserved. …

Ashraf Koheil, Regional Sales Director, MEA HQ at GROUP-IB, tells Anita Joseph that education and awareness of the end user …

By Gregg Petersen, Regional Director – MEA at Cohesity The Middle East has quickly embraced cloud technology, with a huge …

Layale Hachem, Senior Solutions Engineer – BeyondTrust Do you know anyone who has clicked an unknown link in an email? …
GET TAHAWULTECH.COM IN YOUR INBOX