It may be old news now, but hackers are still using news of the royal baby’s birth to entice people into clicking on malicious links, according to researchers at Trend Micro.


It may be old news now, but hackers are still using news of the royal baby’s birth to entice people into clicking on malicious links, according to researchers at Trend Micro.

Distributed Denial of Service (DDoS) attacks are getting bigger, but their duration are getting shorter, according to an analysis released …
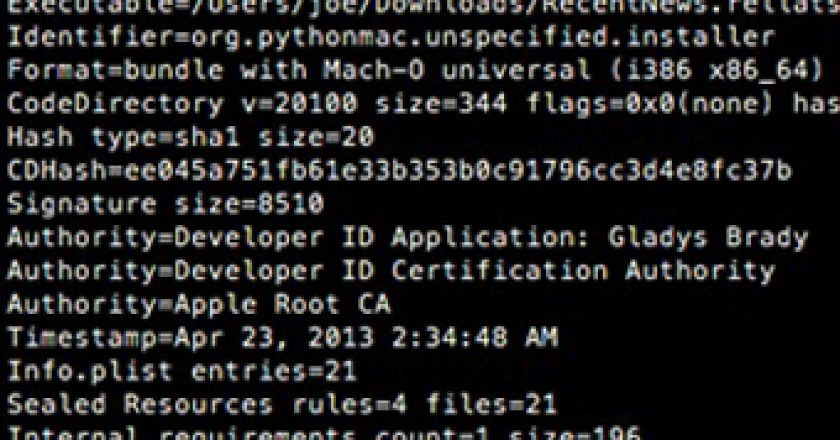
Researchers at F-Secure have discovered malware targeting OS X, which leverages a technique called right-to-left override (RLO) in order to spoof its malicious nature.

Companies and organisations should ensure that they have a full 360-degreee view of their data, says AccessData’s Paul Wright.

The creation of Android malware is now mature enough for there to be development cycles that mimic those of the legitimate software world, a report from Juniper Networks has concluded.

The source code for the Carberp banking Trojan program is being offered for sale on the underground market at a very affordable price.

Revelations over the U.S. National Security Agency’s Prism surveillance programme have much of the general public in uproar, but in terms of the controversy’s impact to enterprise IT, some CIOs have measured, albeit watchful reactions.

Enterprises should be on the look out for increased security threats during the holy month of Ramadan, which begins on …

StarLink on Tuesday announced that it had been signed as master distributor for Guidance Software in the Middle East. The …

With the world on constant alert for cyber attacks, CIOs and IT decision makers flooded to the Habtoor Grand hotel …
GET TAHAWULTECH.COM IN YOUR INBOX