Submarine cables are the unseen lattice that make communication across the globe possible. Their impact is felt by Internet and mobile users everywhere. How will this network of cables grow in the future?
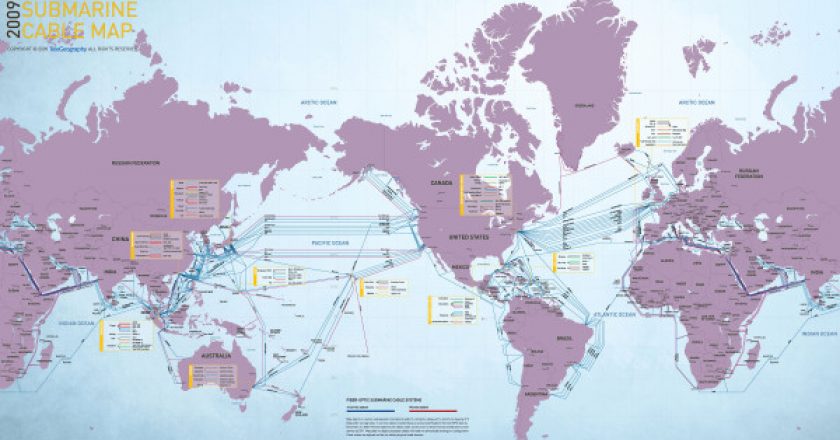


Submarine cables are the unseen lattice that make communication across the globe possible. Their impact is felt by Internet and mobile users everywhere. How will this network of cables grow in the future?

EMC has released the findings of a survey that asked I.T. decision makers in UAE for their perspective on I.T.’s role as an enabler of business change during the shift towards the megatrends of cloud, mobile, social and Big Data.
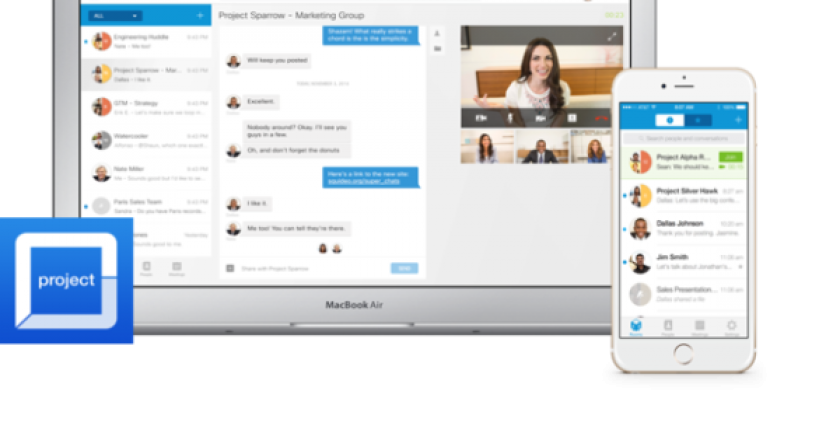
Cisco will package and deliver enterprise collaboration capabilities via a mobile and Web app built to replicate the ease of use of consumer software but designed for ad hoc, workplace team interaction.

Once a seething cauldron of competition, the twice-yearly Top500 listing of the world’s most powerful supercomputers has grown nearly stagnant of late.
Intel will combine its PC and mobile processor divisions under one roof, reflecting a changing market in which the line between tablets and laptops has blurred.

Growing usage of mobile services, economic growth and the increased affordability of devices is expected to push Africa’s mobile subscriber base to 975 million by 2020.

BlackBerry has announced a renewed enterprise focus, including a partnership with Samsung that provides secure mobile software for certain Samsung Android smartphones and tablets.
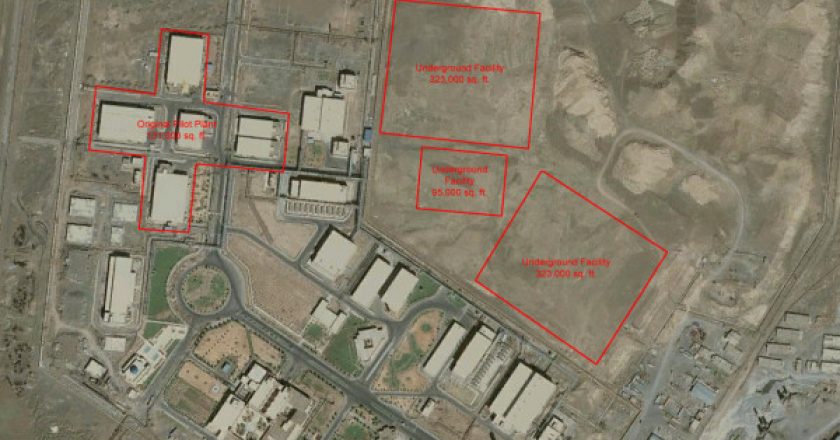
Stuxnet, the powerful malware that wormed its way in and hobbled Iran’s uranium enrichment efforts, infiltrated the secure networks of the nuclear program via trusted partners, newly public information reveals.

The Technical Vocational and Training Corporation, headquartered in Riyadh, Saudi Arabia, lacked a solution to allow its 150 campuses to be connected with access to critical data and information. Huawei’s Cloud OS has since linked all campuses to a central educational resource portal.
More than three years after acquiring Skype, Microsoft today said it would rebrand its semi-rival Lync corporate communications platform as “Skype for Business.”
GET TAHAWULTECH.COM IN YOUR INBOX