Oracle and Microsoft Announce Availability of Oracle Database Service for Microsoft Azure.


Oracle and Microsoft Announce Availability of Oracle Database Service for Microsoft Azure.

Trellix releases Summer 2022 threat report – Business Services Top Target of Ransomware Attacks.

OutSystems Joins SAP PartnerEdge Program to Support SAP S/4HANA Migration.

Vectra AI Strengthens Leadership Team with New Chief Marketing Officer.

The Planning Survey 22: Jedox named the number 1 global planning software providing business value.

Microsoft and Majid Al Futtaim aim to partner to empower regional startups.

Microsoft launches HoloLens 2 in the UAE, empowering organisations with the innovation of mixed reality.

Cloud transformation with Huawei helps carriers achieve new growth.
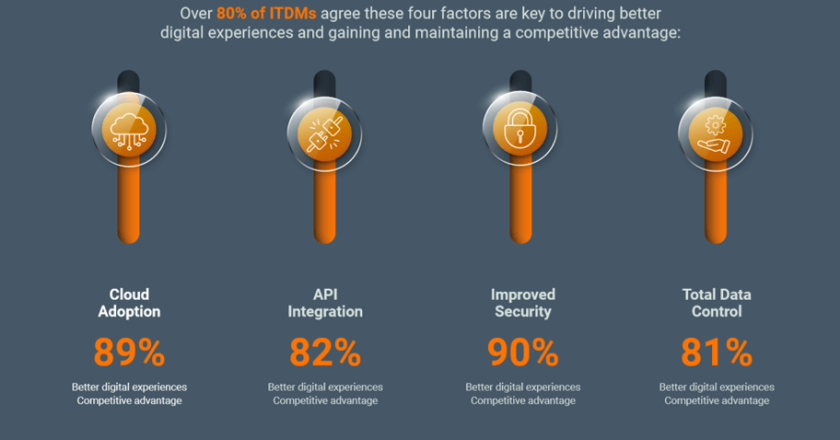
Among IT Decision-Makers, 85% See Urgent Shift in Focus to Consumers’ Digital Experiences in New “Reprogramming the Enterprise” Report from WSO2.

New Technology Systems LLC, Intertec Systems, Konvexe, Block Armour, and Blockchain Worx announce strategic partnership to expand blockchain-based enterprise solutions in the middle east region.

Cisco Delivers Simpler, Smarter Networks with a More Unified Experience.

3 Things Business Leaders Should Know About Security.

Dubai, UAE, July 18th, 2022: Help AG, the cybersecurity arm of e& enterprise (formerly known as Etisalat Digital) and the …

Osama Qadan, Technology panelist at CPI, shares his on the challenges faced by SIs in the post-COVID era System Integrators …

Lenovo and etisalat by e& Develop 5g Edge-In-A-Box Solution to Support Smart Cities, IoT and Rapid 5g Connectivity.

Veeam: A Good Security Strategy Against Ransomware is at the Heart of Digital Transformation.
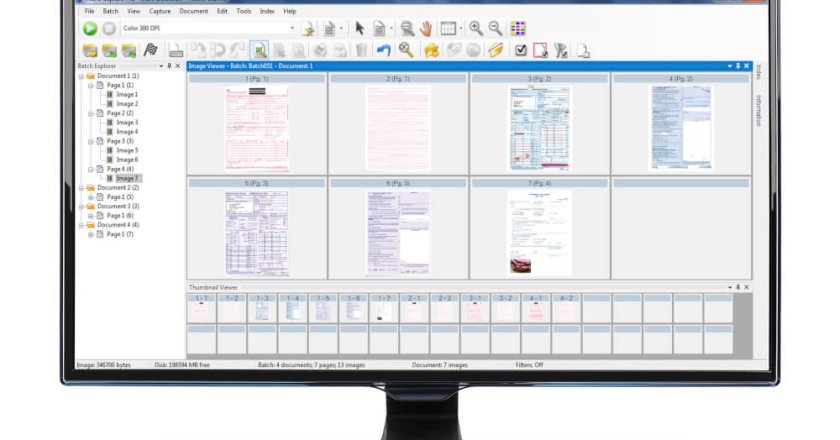
Kodak Alaris Releases Next-Generation Capture Pro Software.

(HPE Aruba): Preparing Businesses for the Next Wave of Digital Transformation.

Tenable Introduces Nessus Expert with External Attack Surface Management and Cloud Security Capabilities.

Create a Data Fortress for Protection against Ransomware Attacks.