Christos Tulumba, Chief Information Security Officer at Veritas Technologies, has penned a comprehensive op-ed designed to provide CISO’s with a …


Christos Tulumba, Chief Information Security Officer at Veritas Technologies, has penned a comprehensive op-ed designed to provide CISO’s with a …

Anita Joseph caught up with Eugene Kaspersky, Founder and CEO of Kaspersky, during the inauguration. Kaspersky Transparency Center, the first …

Industry’s largest repository of threat, vulnerability and asset data enables unprecedented intelligence to quickly identify and mitigate cyber risk.

More than half (53%) feel unprepared to cope with a targeted attack, up from 47% the previous year.

It Takes Less Than a Day for Attackers to Reach Active Directory—Companies’ Most Critical Asset. The Vast Majority of Ransomware Attacks Occur Outside of Business Hours.

Shorter Attacker Dwell Times Require Faster Response, as Indicated in Sophos’ New Active Adversary Report for Tech Leaders.

OPSWAT’s 2023 Threat Intelligence survey highlights the urgent need for enhanced detection capabilities to combat evolving malware threats.
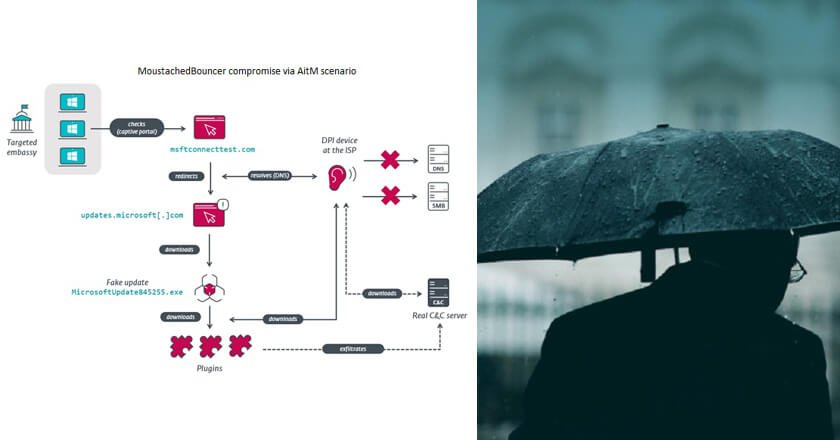
MoustachedBouncer is a threat group, recently discovered by ESET researchers, which specialises in the espionage of foreign embassies, including European ones, in Belarus. It is very likely aligned with Belarus interests.

Taj El-khayat, Area VP, South EMEA, Vectra AI reveals GCC’s $7.45M ransomware impact overshadows global averages, fueling demand for AI-powered …

Trellix Advanced Research Centre’s investigation exposes serious vulnerabilities in CyberPower’s DCIM platform and Dataprobe’s iBoot PDU, highlighting potential unauthorized access …

Industry’s largest repository of threat, vulnerability and asset data enables unprecedented intelligence to quickly identify and mitigate cyber risk.

To stay competitive, it’s essential for organisations to adopt AI technology while safeguarding against potential risks. By taking these steps now, companies can ensure they’re able to reap the full benefits of AI while minimising exposure.

Provides organisations with a 360-degree view of all identities and privileges to eliminate blind spots and shut down attack pathways.

Vectra AI introduces the Vectra AI Platform with Attack Signal Intelligence™, empowering security teams to combat complex hybrid attacks and …

Many believe they can tolerate the stress of the role; however, burnout in the form of chest pains or panic attacks is very real. Burnout happens suddenly when an often-inconsequential event becomes the step too far, causing a catastrophic breakdown.

Layale Hachem, senior solutions engineer at BeyondTrust explains how businesses can defend against IABs by enforcing least privilege, enhancing multi-factor …

Cybercrimes and information security breaches discriminate no one, and the healthcare sector is no exception. With enhanced data storage of …

Anita Joseph caught up with Mohamad Sabra, SMB Lead, Middle East and Africa at Cisco, to find out how the …

With the explosion of digitisation across industries, opportunities for fraud and financial crime have grown exponentially.

Because MFA is a significant improvement over password-only authentication, it is here to stay, so cybersecurity practitioners must address its vulnerabilities.