CNME’s prestigious Network World Middle East awards honoured the region’s top networking talent last night at the Safinah Ballroom in Jumeirah Beach Hotel, Dubai.


CNME’s prestigious Network World Middle East awards honoured the region’s top networking talent last night at the Safinah Ballroom in Jumeirah Beach Hotel, Dubai.

Many recent studies of security vulnerabilities come to the same conclusion: The human factor is a greater risk to organisations than flaws in technology.

Cellular networks in the Middle East will need fatter pipes to the wired Internet to keep delivering a satisfying mobile experience, and fibre is emerging as the best for mobile backhaul networks.
Global Distribution has signed an agreement with Synology to distribute the range of Network Attached Storage (NAS) server products in GCC and Africa.
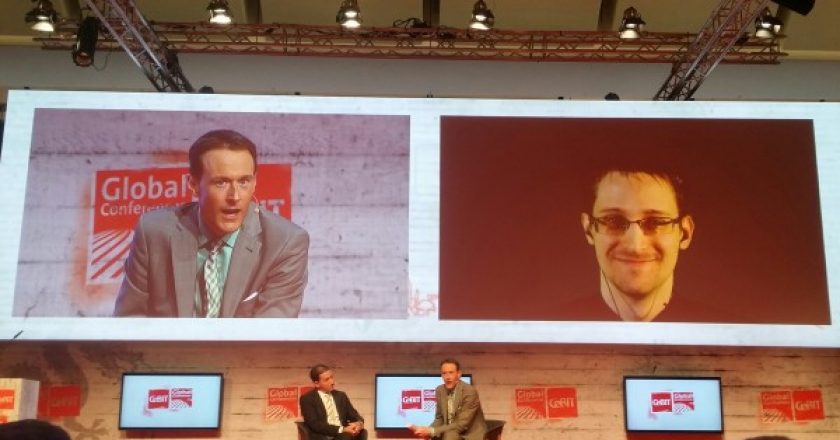
National Security Agency whistleblower Edward Snowden joined journalist Glenn Greenwald to complete the lineup at day three of CeBIT 2015 with a Q&A session at the Hannover trade show.

Ideal for building Ethernet fabrics in demanding environments, with the company’s VCS Fabric technology, the Brocade VDX 6940 simplifies network design and operations for both cloud and Big Data network fabrics.

Huawei today launched four new networking, storage and security solutions at Hannover’s CeBIT 2015 trade show.
The relationship extends from the Middle East and includes France, Spain, Sweden, Denmark and South Africa. As per the agreement, WestconGroup will distribute Aruba’s portfolio of access management, network infrastructure and mobile engagement solutions through its extensive network of resellers and systems integrators across these regions, enabling regional organisations to create next-generation wireless networks.

The President of Huawei’s Enterprise Business Group used his keynote slot at CeBIT 2015 to highlight the company’s strategy for transitioning to Industry 4.0.

Samsung has today launched its Samsung Business division – that unifies its end-to-end business solution portfolio – at the CeBIT 2015 conference in Hannover, Germany.

Etisalat recently organized a half-day workshop highlighting how the service provider’s could protect businesses in the energy and utilities sector from market volatility and unforeseen business circumstances.

SAP CEO Bill McDermott kicked off Hannover’s CeBIT 2015 technology trade show by underlining the importance of a versatile digital economy in a one-on-one Q&A session.

State sponsored malware is becoming increasingly sophisticated according to a report released by security vendor, Kaspersky Labs. According to a company statement, this new trend was confirmed during analysis of the EquationDrug cyber-espionage platform, the main espionage platform developed by the Equation Group.

Amazon.com has acquired 2lemetry, a startup that has developed a platform for the integration of connected devices across enterprises, as it expands on its Internet of Things strategy. The current customers of 2lemetry will continue to be supported, with the name and branding retained.

Alan Matthews, Chairman, Rapid7 believes in deleting emails. He strongly suggests not hoarding unused data, like old correspondence that can be mined by cyber-criminals and used against you. CNME sits down with Matthews to see what other suggestions he has to keep our data safe.
The adoption of virtualisation in the past few years has undoubtedly changed the face of the data centre. No longer housed in sprawling warehouses, data centres are fast becoming slimmed down and agile.

There is no question that the use of mobile devices, both personally and professionally, are now not only convinient, but necessary for productivity. As the mobile technology develops, mobile security best practices must also adapt.

Launched in 1992 by the U.S. Environmental Protection Agency, ‘Energy Star’ was the initiative that kick-started green IT. Since then, minimising the negative impact of information technology use on the environment has become increasingly pertinent in the age of sustainability.

HP has said that it is creating a server family aimed specifically at building systems for cloud providers.

Researchers sponsored by the U.S. government have reportedly tried to defeat the encryption and security of Apple devices for years.