The person responsible for disclosing details on the growth of U.S. government surveillance programmes that exploded into public view last …


The person responsible for disclosing details on the growth of U.S. government surveillance programmes that exploded into public view last …

Enterprises are under heavy pressure to change their approach to IT security because of a “nexus of forces” that include …

Cisco has overtaken IBM as the leading provider of infrastructure for cloud computing, analysts at Synergy Research reported on Monday. Synergy …

The first three months of 2013 have seen a surge in spam volume, as well as large numbers of samples …
A lot has been said about Nokia in recent months – a great performance, by all accounts, in the last two quarters, showing strong growth on its recently self-proclaimed flagship device; the Lumia 920.

If you’re worried that a disgruntled former coworker will hack your LinkedIn account and add embarrassing details to your resume, …
A 17-year-old German student contends PayPal has denied him a reward for finding a vulnerability in its website. Robert Kugler …

Seeing a “404 error” or the Twitter “Fail Whale” can really kill a good online buzz. Those kinds of service …
Yahoo again ranks as one of the world’s 100 most valuable brands. The Internet company nabbed the 92nd spot in …

Few phenomena have been so widely discussed yet remain so puzzling as the world of Bitcoins. Businesses galore are now …

Attendees flooded the Habtoor Grand in Dubai today as CNME played host to the region’s first ever dedicated big …
A session on market insights at BlackBerry Live aimed at providing an overview, as well as an insider’s perspective, to …
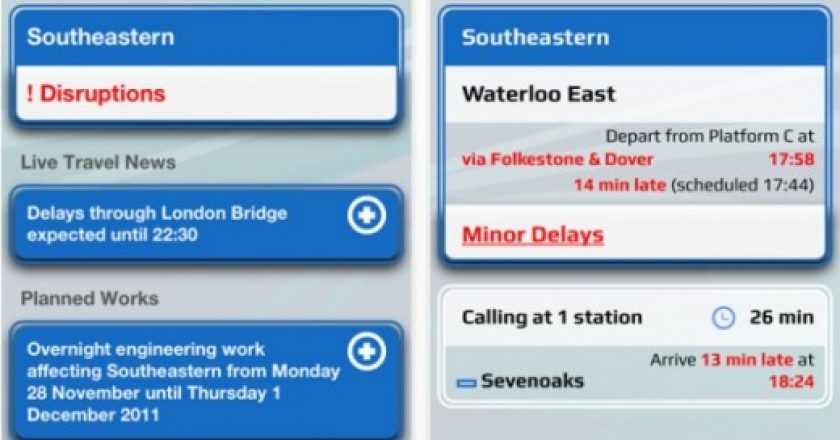
Google in east London hosted a two day “hackathon” last month to help demonstrate how open public sector data can …

The combination of highly virtualised environments inside enterprise networks, along with an explosion of mobile traffic, are exposing the limitations …

This week was a week for email milestones. Spam – that scourge of the Internet – turned 35 years old. And …

The popular Snapchat photo-messaging app used mainly by Android and iOS mobile device owners to share images that then self-destruct …

The Dutch government on Thursday presented a draft bill that aims to give law enforcement the power to hack into …

As we’ve become a more mobile society—working from virtually anywhere on our smartphones and tablets—we’ve also embraced various cloud storage …
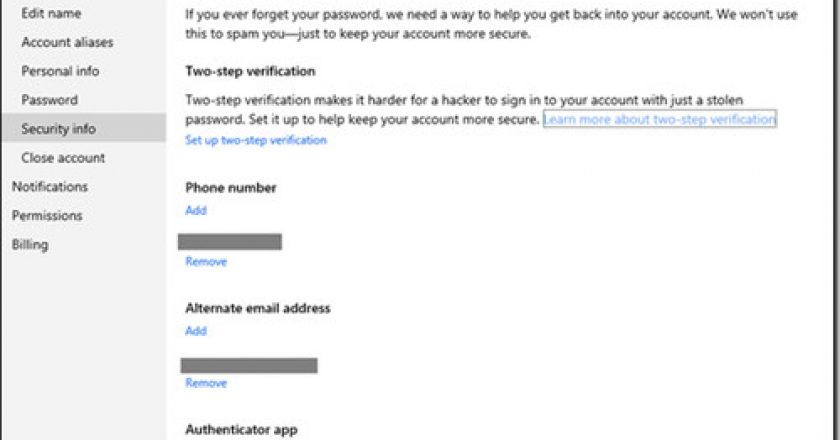
Following similar initiatives by Apple, Google and Facebook, Microsoft is enabling two-factor authentication for its Microsoft Account service, the log-on service for …

Microsoft’s top executive for mobile phones took shots at both iOS and Android on Tuesday, calling Apple’s operating system “boring” …