Resist or go with the flow? The BYOD boom may bring new security challenges but it is the reluctant businesses …

Shifra completes roadshow with Proofpoint, Centrify and Stonesoft
Value-added distributor Shifra has completed a Middle Eastern roadshow with partner-vendors Proofpoint, Centrify and Stonesoft, the firm announced on Saturday. …

North Korea suffers 36-hour Internet outage
Internet connectivity in North Korea was restored on Friday following a 36-hour outage that the country’s official media blamed on …
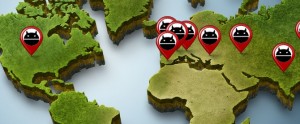
China, India top malware ‘victims’ in Asia Pacific
China and India were the top two “victim” countries in the Asia Pacific, according to a recent Web threat report. …

Experts slam ‘dangerously unprepared’ IT security managers
Companies with IT security strategies that focus mostly on complying with key standards are dangerously unprepared for emerging cyber threats, …

Malware-as-a-service market sees rise in services
Prices are falling and the number of services is increasing as developers in the online underground compete fiercely for criminals …
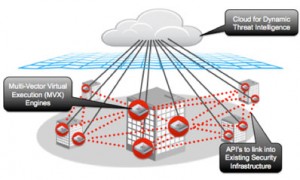
FireEye launches new threat protection platform
Security company, FireEye, has announced a new threat protection platform designed to help enterprises deploy new security models to counter …
HP outlines Big Data Security strategy
HP on Monday unveiled its Big Data Security strategy, describing how combining the enterprise search and knowledge management resources from its Autonomy subsidiary …

Dell comes out fighting
Dell executives went on the offensive this week, claiming that the firm can trump Cisco in the information technology security market, as …

China denies involvement in hacking
China’s Ministry of National Defence on Wednesday denied recent accusations that the nation’s military supports cyber espionage, saying that a …

Apple infected by Java-based malware
Apple on Tuesday said that some computers belonging to its employees had been targeted by hackers originating from China – …
Steady as it goes
Symantec has recently laid out its management and product strategy. The company, which has gone through a leadership change, is …

Symantec – Security and storage predictions for 2013
In 2012 mobility, virtualisation and cloud computing were three big trends that affected change in the way organisations across the …

Getting worse
With the problem of hacking and its consequences on enterprise only exacerbating, CNME rounds up the views and tips from …

EMC to buy web intelligence provider Silver Tail Systems
EMC said today it has agreed to buy privately-held start-up Silver Tail Systems, a vendor of real-time web session intelligence and …

Blue Coat to address ‘urgent and complex issues’ at GITEX
Blue Coat has announced it will be demonstrating its entire suite of application delivery networking solutions at GITEX, in order …

Analysts blame politics, not security, for Huawei, ZTE allegations
A year-long investigation by a U.S. congressional committee has reportedly concluded that Huawei Technologies and ZTE pose a security threat …

Iran blocks Gmail and Google, security researchers say
The Iranian government appears to have blocked access to Google’s search engine and Gmail webmail service from inside Iran, according …

Blue Coat to demonstrate WAN optimisation, Web-security solutions at GITEX
Blue Coat Systems, a market and technology leader of Web security and WAN optimisation solutions, has announced its participation at …

Future warfare could be online, experts say
Future warfare could be fought by soldiers using bullets and bombs as well as people hunched over laptops according to …


