SAP will invest AED 1.65 billion on a four-year growth plan in MENA, which it referred to as “the fastest …


SAP will invest AED 1.65 billion on a four-year growth plan in MENA, which it referred to as “the fastest …

Spammers are abusing a Dropbox feature that lets users share a shortened link, directing people to websites selling questionable pharmaceuticals, …

Network specialist Ciena Corporation today announced WaveLogic 3, the industry’s first software-programmable coherent technology that scales to 400 Gb/s. Ciena …

Cloud computing price cuts by Google, Amazon and now Microsoft may indicate that businesses are discovering that moving to the …

Blue Coat Systems today issued its Blue Coat 2012 Web Security Report that identifies and analyses trends in malicious attacks …

Security plays a hugely influential part in our lives. On a normal morning we’ve encountered it on numerous occasions before …

The Department of Economic Development (DED) in Dubai has awarded a contract to Al-Futtaim Technologies, one of the region’s leading …

The story of this Sony factory, which took the full brunt of a powerful tsunami that washed through a year …

Data at rest has long been protected by technology called public key infrastructure (PKI), in which data is encrypted when …

Proponents of a common scheme for managing user identity in cloud-based applications will pitch their idea to the Internet’s premier standards-setting body …

The division of Sony that suffered a cyber attack last year, which led to a major PlayStation network outage and …

IT considerations are not given adequate attention in the due diligence prior to mergers and acquisitions, according to research from …

Startup vendor StopTheHacker has added a feature to its subscription security service that automatically removes malicious code placed on Web …

Intel is working to boost data transfer speeds with a faster pipe on Thunderbolt, a high-speed connector technology that link …

The latest release of Apple’s pervasive iPad tablet, simply called ‘The New iPad’, has benefited from some technical upgrades that …

Emitac Enterprise Solutions today announced that it has achieved Symantec specialisations in the areas of Data Protection and Archiving and …
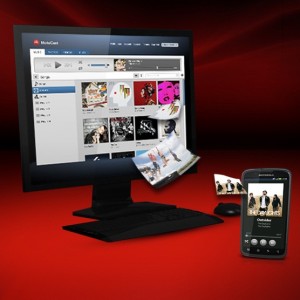
A new application provides access to a user’s music, photo and video computer libraries from a Motorola RAZR smartphone anywhere …

Symantec today announced new cloud-based data solutions, which it said deliver a new approach to modernising backup and recovery for …

A new survey from IBM finds that while only 13% of businesses have substantially implemented cloud-based offerings, they are expected …

IBM has taken the secure USB stick concept to its logical extreme, announcing a pilot service capable of streaming an …