96% of security analysts in the UAE and KSA fear they are missing a relevant security event according to new …



96% of security analysts in the UAE and KSA fear they are missing a relevant security event according to new …

This spike reflects a similar trend in the Middle East region, which projected a two-fold hike (103%) in Rootkit detections, as compared to the first five months of last year.

Attacks on Middle Eastern government agencies are mainly carried out by APT groups (56%), covertly establishing themselves in the victim’s infrastructure for the purpose of cyberespionage.

Ezzeldin Hussein, Sales Engineer Director at SentinelOne tells Anita Joseph how the role of the CISO has evolved from being …
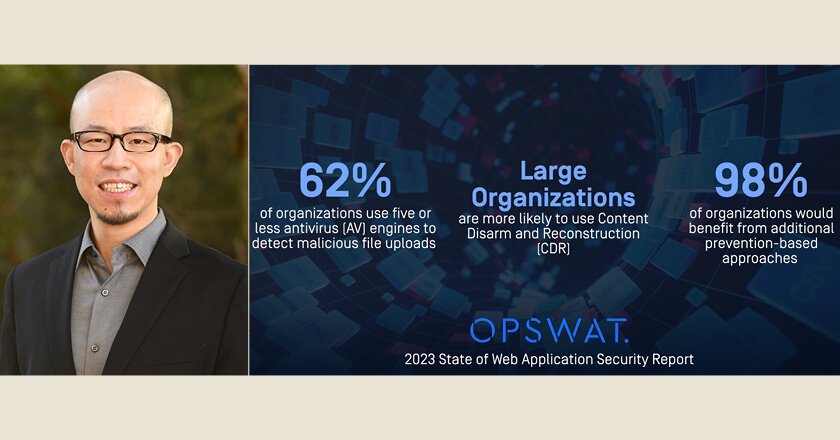
With at least 75% of Organisations Upgrading Infrastructure and 78% Increasing Security Budgets, OPSWAT’s Latest Report Highlights Disparity Between Infrastructure Upgrades, Spending and Security Improvements.

On Artificial Intelligence Appreciation Day, Anita Joseph, Editor, Tahawultech.com, spoke to technology industry visionaries to find out what they think …

Vibin Shaju, VP Solutions Engineering EMEA at Trellix, explains how XDR is crucial for cybersecurity in GCC as organizations seek …

As the automotive industry moves towards a future of connected and autonomous vehicles, ensuring robust cybersecurity is of paramount importance. …

Ransomware is the only form of cryptocurrency-related crime that has grown in 2023, with attackers on pace for their second-biggest year ever.

Kaspersky unveils a comprehensive report highlighting the increasing peril faced by small and medium-sized businesses (SMBs) in the current cyberthreat landscape.