Trellix Advanced Research Centre’s investigation exposes serious vulnerabilities in CyberPower’s DCIM platform and Dataprobe’s iBoot PDU, highlighting potential unauthorized access …



Trellix Advanced Research Centre’s investigation exposes serious vulnerabilities in CyberPower’s DCIM platform and Dataprobe’s iBoot PDU, highlighting potential unauthorized access …

Provides organisations with a 360-degree view of all identities and privileges to eliminate blind spots and shut down attack pathways.

New Cloud Native Detection and Response capabilities provide security teams with real-time, unified visibility and context into containers and Kubernetes environments.
Proofpoint researchers identified a new malware call WikiLoader. It was first identified in December 2022 being delivered by TA544, an actor that typically uses Ursnif malware to target organisations.

Anita Joseph caught up with Viswanath Pallasena, CEO of Redington Middle East and Africa, to hear the captivating story of …

Cybercrimes and information security breaches discriminate no one, and the healthcare sector is no exception. With enhanced data storage of …
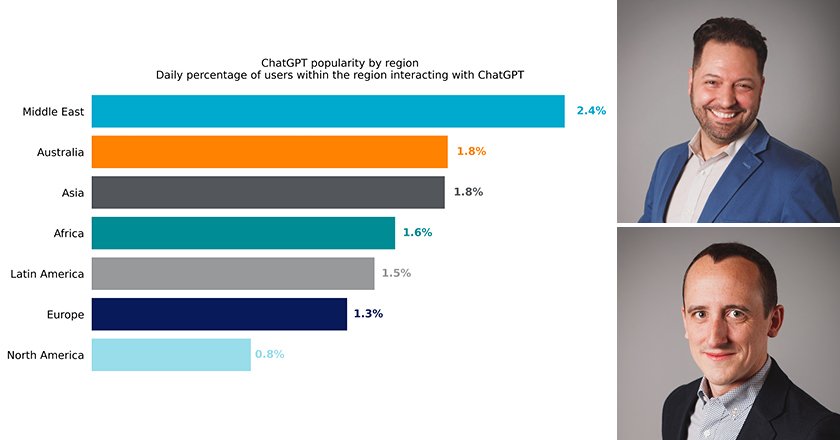
Within the average large enterprise, sensitive data is being shared to generative AI apps every hour of the working day.

Anita Joseph caught up with Mohamad Sabra, SMB Lead, Middle East and Africa at Cisco, to find out how the …

Veritas Technologies, the leader in secure multi-cloud data management, is building on their existing relationship with Microsoft to deliver a …

Anita Joseph caught up with Chris Bihary, CEO & Co-Founder of Garland Technology and Manu Nair GM of Oregon Systems, …