 A malicious software program found in ATMs in Mexico has been improved and translated into English, which suggests it may be used elsewhere, according to security vendor Symantec.
A malicious software program found in ATMs in Mexico has been improved and translated into English, which suggests it may be used elsewhere, according to security vendor Symantec.
Two versions of the malware, called Ploutus, have been discovered, both of which are engineered to empty a certain type of ATM, which Symantec has not identified.
In contrast to most malware, Ploutus is installed the old-fashioned way: by inserting a CD boot disk into the innards of an ATM machine running Microsoft Windows. The installation method suggests that cyber-criminals are targeting standalone ATMs where access is easier.
The first version of Ploutus displays a graphical user interface after the thief enters a numerical sequence on an ATM’s keypad, although the malware can be controlled by a keyboard, wrote Daniel Regalado, a Symantec malware analyst, on October 11.
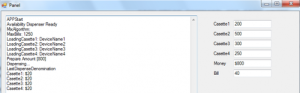
Ploutus is programmed for a specific ATM model since it assumes there is a maximum of four cassettes per dispenser in the ATM. It then calculates the amount of money that should be dispensed based on the number of bills. If any of the cassettes have less than the maximum number of 40 bills, it releases whatever is left, repeating that process until the ATM is empty.
Kevin Haley, director of Symantec Security Response, said in an interview earlier this month that the attackers have deep knowledge of the software and hardware of the particular ATM model.
“They clearly know how this machine worked,” he said.
The source code of Ploutus “contains Spanish function names and poor English grammar that suggests the malware may have been coded by Spanish-speaking developers,” Regalado wrote.
In a new blog post, Regalado wrote that the attackers made Ploutus more robust and translated it into English, indicating the same ATM software can be exploited in countries other than Mexico.
The “B” variant of Ploutus has some differences. It only accepts commands through the keypad but will display a window showing the money available in the machine along with a transaction log as it dispenses cash. An attacker cannot enter a specific number of bills, so Ploutus withdraws money from the cassette with the most available bills, Regalado wrote.
Symantec advised those with ATMs to change the BIOS boot order to only boot from the hard disk and not CDs, DVDs or USB sticks. The BIOS should also be password protected so the boot options can’t be changed, Regalado wrote.





