Mimecast threat intelligence analysts discovered a list of more than 15,000 stolen credentials for freemail accounts that were uploaded to a public facing website in October 2019.
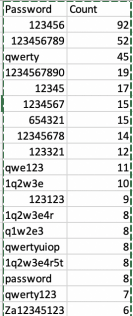
The top password was ‘123456’ with 92 occurrences. The top 20 list indicates that simple, easily guessed passwords are still widely used.
The average password length was 8.8 characters. The distribution of password lengths is shown below. There were 3621 passwords of length 8. 217 passwords had only 5 characters. Only 10% of accounts have passwords with more than 12 characters.
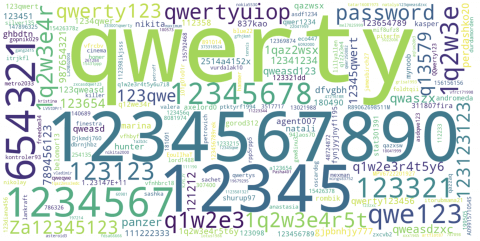
The average password length was 8.8 characters. The distribution of password lengths is shown below. There were 3621 passwords of length 8. 217 passwords had only 5 characters. Only 10% of accounts have passwords with more than 12 characters.
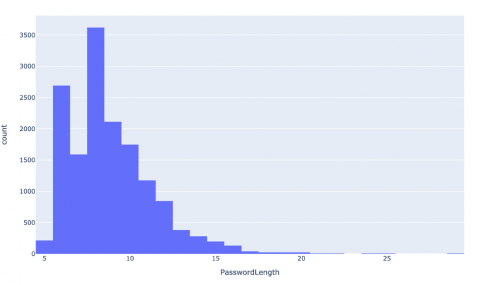
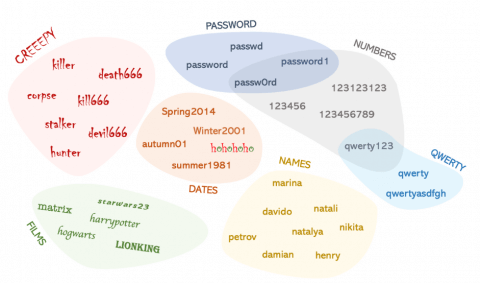
The diagram below shows a selection of some of the common or easily guessed passwords found in the list.
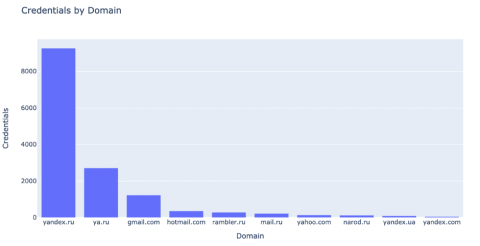
The paste included credentials for accounts from 230 domains. The top 10 domains are shown below.
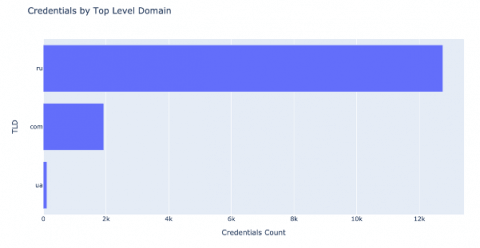
Analysis of the top-level domains shows that the most common top level domain (TLD) is .ru. The top 3 TLD’s are shown below.
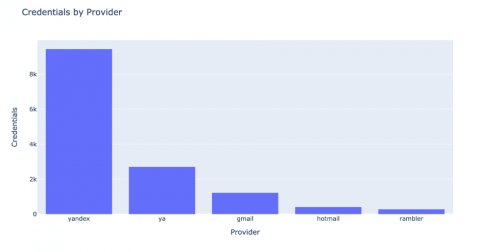
The top mail provider was Russian based, Yandex mail
Dr. Kiri Addison, Head of Data Science for Threat Intelligence and Overwatch, Mimecast, said, “A weak password is often the first line of attack that opportunistic and malicious intruders target when looking to steal or collect user data. With more people working remotely due to COVID-19 and accessing corporate and business accounts outside of the office, people need to be even more careful with their passwords – and that means avoiding the classic ‘123456’ password that is unfortunately still too common. Luckily, there are simple solutions to avoid this: for example, using a password manager naturally encourages people not to use the same passwords, Instead, the system records original, complex passwords that the user can then access using a master password, this helps takes away the pressure of remembering every single password. Combined with multi-factor authentication, which provides an additional layer of security and a further barrier from unwanted access, users can benefit from higher security.
As more services move to the cloud and breaches become larger and frequent, individuals and enterprises cannot afford a lack of foresight when it comes to password security. This is where businesses have a role to play: by implementing strong cyber hygiene practices that include awareness training of the risks, they can help their staff better understand how they can keep themselves safe online. Poor cyber hygiene practices are simply not something any business can risk today, particularly as they rely on distributed workforces.”





