Rawad Darwich, regional sales manager, Fidelis Cybersecurity, discusses why it’s time to re-imagine the security stack.
Data security is still the number one IT concern for businesses worldwide. A research carried out by ThoughtWorks in 2019 revealed that 33 percent of UK business leaders said that ‘data safety and cyber risk’ was a bigger concern than the challenges of Brexit. Roll on six months and those concerns have increased exponentially as millions of people are now working from home due to the coronavirus pandemic. The story is the same for businesses in many countries across the globe and to address this, CIOs and CDOs are consistently ‘adding’ bolt-on security measures.
As new threats emerge, organisations add to their security stack by bolting on more cybersecurity tools. Combine the fact that many of the security ‘solutions’ are from different vendors with the problem of under-utilisation, not only are there a range of capabilities that are redundant but the organisation’s entire security measures are complex and offer little to no benefits. Here’s a fact from Fidelis Security’s latest survey: less than seven percent of respondents were using their full security stack. Now that’s a worrying statistic.

The negative impact of too many security layers
As technology advances, so does the threat level to businesses, which push them to be more reactive in dealing with the resulting cybersecurity issues. There has often been the situation whereby security tools have been implemented in order to address a specific problem with little thought as to how that integrates with existing systems. Fidelis found that some organisations have as many as 75 different cybersecurity tools in use, ranging from various firewalls and antivirus tools to intrusion detection and intrusion prevention tools, advanced threat protection tools and single-purpose endpoint agent technologies.
In the drive towards digital transformation, magnified in recent months, this multi-layered Defense-in-Depth approach has morphed into Defense-in-Death as CIOs, CDOs and IT teams are discovering widespread under-utilisation. Couple that with a lack of automation and few cybersecurity professionals available, SOCs are struggling to deal with the influx of alerts from each and every cybersecurity tool, with many of those alerts having little or no context.
Ultimately, this reactive approach will impact response time but more worryingly, as the capabilities of each security tool overlaps with another, more layers of complexity are added resulting in little to no benefit in terms of overall security against cyber threats. Many businesses lack a comprehensive streamlined security infrastructure that provides real time visibility of their cyber-attack surface, or little understanding of their critical asset vulnerabilities.
Re-thinking the security stack
Security stacks are overloaded; SOCs are dealing with an infrastructure that is fragmented and too complicated, leaving them bouncing from one issue to another without the time and resources to identify the actual threat and resolving it successfully.
• Threat levels are rising, and changing in the new modern world. Businesses are facing several security challenges:
• A lack of real time visibility of their cyber-attack surface.
• A lack of automation of security systems and processes.
• Little or no threat intelligence tailored to the business.
• Few cybersecurity professionals’ available, creating big skill gaps within the business.
Unmanageable, complicated, overcrowded security stacks that leave little time and resources to address modern-day cybersecurity threats.
Change is needed, and fast. This isn’t lost on the security industry or businesses today. On the positive side, Fidelis Security’s recent research demonstrated that there is a thirst for change with 78 percent of respondents admitting that they have, or are planning on, consolidating their security stack.
The security landscape has significantly changed, particularly in the last six months, and demand for unified security software solutions is high. Today, businesses are adopting automation capabilities to provide broader real time visibility into their networks and optimising digital workflows. But there is also a need to focus on people; given the right tools, people become threat hunters, discovering malware or suspicious activity that may be missed by other security solutions. With consolidated security stacks, threat hunters are able to effectively identify, analyse and resolve unknown cyber-threats.
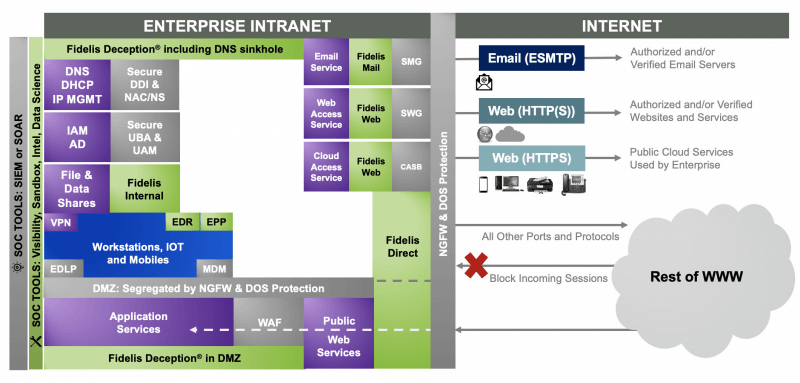
Conclusion
By analysing and simplifying the existing cybersecurity stack, optimising their full capabilities in a focused, measured way, security professionals will be able to identify, manage and respond to the business’s threat landscape effectively including:
• Addressing security methods and network endpoint visibility that detects and identifies internal and external threats.
• Securing the enterprise network perimeter, protecting internet access points and providing a network traffic analysis that records all activity.
• Managing cloud and web-based applications to streamline data traffic and secure workloads.
It’s time to enable IT teams and SOCs with the right tools so they can do their job. The cyber battle will only be won through the consolidation of security stacks that deliver the right set of capabilities, enabling businesses to continuously detect, respond and protect their critical assets.





