In its July patch day, SAP released 20 new or updated Security Notes. While the number of critical notes was very moderate compared to the last patch days with “only” two HotNews notes and two High Priority notes, it was a patch day that required maximum attention from all SAP customers. SAP published patches for the extremely critical RECON vulnerability (CVSS Score of 10.0) that affects all SAP applications running on SAP NetWeaver AS Java and strongly recommends immediate patching.
Due to its criticality and thanks to the fast reaction of the SAP Security Response Team after Onapsis reported the flaw, SAP provided a fix within only a few weeks. SAP Security Note #2934135, tagged with the highest possible CVSS Score of 10.0, was published in the SAP July Security Notes and provided the corresponding patch. RECON (Remotely Exploitable Code On NetWeaver) affects more than 40,000 SAP customers, with increased exposure for internet-facing systems.
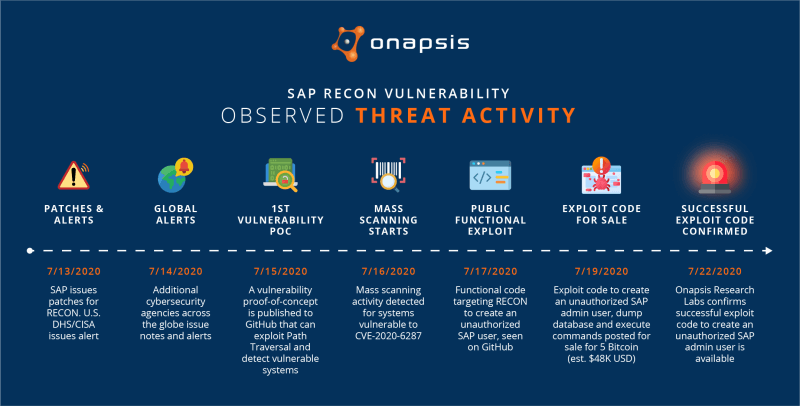
Given the severity of this vulnerability, the U.S. Department of Homeland Security issued a US-CERT Alert, AA20-195A, in coordination with BSI CERT-Bund and followed by other global organisations, providing warnings about potential threats associated with this vulnerability.
The RECON vulnerability that was discovered by Onapsis affects a core component that is included in the SAP Java NetWeaver layer. It can be exploited by remote unauthenticated attackers and therefore all systems exposed to untrusted networks such as the internet represent a potential attack target. The list of directly affected SAP applications is quite large:
- SAP Enterprise Resource Planning (ERP)
- SAP Supply Chain Management (SCM)
- SAP CRM (Java Stack)
- SAP Enterprise Portal
- SAP HR Portal
- SAP Solution Manager (SolMan) 7.2
- SAP Landscape Management (SAP LaMa)
- SAP Process Integration/Orchestration (SAP PI/PO)
- SAP Supplier Relationship Management (SRM)
- SAP NetWeaver Mobile Infrastructure (MI)
- SAP NetWeaver Development Infrastructure (NWDI)
- SAP NetWeaver Composition Environment (CE)
- Others
With SAP NetWeaver Java being a fundamental base layer for several SAP products, the specific impact would vary depending on the affected system. In particular, there are different SAP solutions running on top of NetWeaver Java which share a common particularity: they are hyperconnected through APIs and interfaces. In other words, these applications are attached to other systems, both internal and external, usually leveraging high-privileged trust relationships.
The way SAP applications are opened to the internet in the form of SAP Enterprise Portals, combined with integration technologies such as SAP SolMan or SAP Process Integration, creates an environment in which the exploitation of a vulnerability with a CVSS Score of 10.0 could ultimately lead to business processes, critical data, personal identifiable information (PII) and financials being compromised.
Once a system is compromised, the possible impact is almost unlimited. Among other things, attackers can create a new user with administrative privileges, allowing them to manage (read/modify/delete) every record/file/report in the system — impacting confidentiality, integrity and availability.
Because of the type of unrestricted access an attacker could obtain by exploiting unpatched systems, this vulnerability also may constitute a deficiency in an enterprise’s IT controls for regulatory mandates—potentially impacting financial (Sarbanes-Oxley) and privacy (GDPR) compliance.
Exploitation of the vulnerability allows an attacker to perform several malicious activities, including:
- Steal personal identifiable information (PII) from employees, customers and suppliers
- Read, modify or delete financial records
- Change banking details (account number, IBAN number, etc.)
- Administer purchasing processes
- Disrupt the operation of the system by corrupting data or shutting it down completely
- Perform unrestricted actions through operating system command execution
- Delete or modify traces, logs and other files
The business impact of a potential exploit targeting RECON could be financial loss, compliance violations and reputation damage for the organisation experiencing a cyber attack.
Given the enormous impact on SAP applications, Onapsis strongly recommends to apply the provided patch. For more details on the RECON vulnerability and the impact of a potential exploit on SAP systems, read the Onapsis RECON Vulnerability Threat Report. Our partner Spectrami looks forward to giving you professional advise, just contact: info@spectrami.com





