 Tuesday’s ransomware outbreak affected victims across the globe from Ukrainian infrastructure including power companies, airports, public transit, and the central bank, as well as the Russian oil giant Rosnoft and Denmark-based shipping company Maersk and pharmaceutical firm Merck, along with organisations in India, Spain, France and the United Kingdom.
Tuesday’s ransomware outbreak affected victims across the globe from Ukrainian infrastructure including power companies, airports, public transit, and the central bank, as well as the Russian oil giant Rosnoft and Denmark-based shipping company Maersk and pharmaceutical firm Merck, along with organisations in India, Spain, France and the United Kingdom.
Whether we term it Petya, NotPetya, ExPetr or GoldenEye, one thing is for sure – experts say this massive cyber-attack is as bad as ransomware gets. Or as some reports suggest, it is much worse than ransomware.
According to UAE-based reseller Data Care’s Sales Director Akash Jain, ransomware can also infect the backup.
He says, “The only proven defense is a snapshot based backup that works at the block level.”
Mohammad Basheer, IT Security Practice Head, ISYX Technologies, says, “Petya ransomware spreads by using two separate exploits.”
Users don’t need to click on anything or take any action, it can spread into the system through the network itself. Therefore, the impact is on a much wider scale and this is why security experts are urging users to update their system to stay protected.
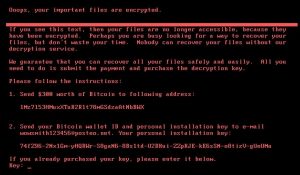
He adds, “The ransomware encrypts a victim’s PC and demands that they pay $300 in exchange for the keys to unlock their computer or lose all their data.”
Sebastien Pavie, enterprise and cybersecurity director, Middle East, Africa and Turkey, Gemalto, says, because many companies, including healthcare and utilities providers are willing to pay ransoms to avoid losing data or having systems shut down, these attacks are increasing.
“This also indicates that ransomware attacks are having an impact on businesses. However, neither businesses nor individuals should pay ransoms to unlock any files that have been affected by a ransomware attack, as this incentivises and rewards these kinds of attacks.”
According to Basheer, this particular ransomware is exploiting a vulnerability in Microsoft Office when handling RTF documents (CVE-2017-0199).
“It also exploits a vulnerability in SMBv1 which is the Microsoft file-sharing protocol. This second vulnerability is described in Microsoft security bulletin MS17-010.”
Jain says if the customer is infected, “there is little anyone can do”. It is much better to have a ‘prevention is better than cure’ strategy.
“Resellers must act proactively to prevent the infection,” he adds.
Ian Jones, divisional director, Westcon Security, says resellers have a responsibility to help ensure that when customers deploy their network security, they regularly also make sure the policies are uniform and up to date.
“Ensure that those enterprises are regularly updating the software on their network and advise if there is software that is end of life or out of date,” he says. “Distributors too can support the reseller community by providing trained engineers to engage with system audits or penetration testing of the end user IT systems to identify if the infrastructure is sound or developed a exploitable hole.”
Although the Middle East hasn’t been touched by Petya yet, industry experts say it could be only a matter of time before it is.
As the Middle East region boasts a huge install base of Windows XP, Jain says, users who haven’t upgraded to Windows 10 may not have patched all vulnerabilities yet.
He says, “We in the Middle East are at as big a risk as any other part of the world.”
Jones adds, “As this is a global attack some enterprises might not even know they have been breached yet or are dealing with the issue quietly. But if anything, we hope that this latest attack makes sure the SISOs and IT managers examine their networks and implement a well thought out, sound and secure policy to mitigate these types of attacks.”
Agreeing Basheer emphasises that no enterprise or individual is exempt from falling victim to a breach because of their size.
“Therefore, rather than being reactive, companies and individuals must be proactive in safeguarding their data – patching and updating the software on network systems, and conduct security awareness programmes.”
The most important aspects when it comes to defending against these types of attacks are education and backup.
“Awareness and education are key aspects in preventing from becoming a victim. Customers should give more importance to backup – even if they are guilty of not patching up the system, they at least have a copy of the data,” Jain says.
According to Basheer, information security professionals can adopt certain measures to help infected customers besides having a backup and using anti-virus.
The first step is to immediately install the MS17-010 patch from Microsoft, he says.
“If you currently run an unpatched Windows system, consider shutting down your machine, if feasible, and leaving it off the network until there is consensus in the research community on what this exploits and how to protect against it,” he adds. “We also recommend you block network access to port 445 on your Windows workstations. You may also want to monitor traffic to that port if you are a security professional.”
Pavie says, “Because data is the new oil in the digital economy, ransomware attacks that restrict access to important data until the attacker is paid are becoming increasingly common. As per the Gemalto 2016 Breach Level Index, 2016 is considered the year of ransomware as these attacks moved mainstream and we expect to see this trend continue this year as well.”





