Huawei Middle East and Central Asia joined a high-level media roundtable on day two of the GSMA M360 EURASIA 2023 …


Huawei Middle East and Central Asia joined a high-level media roundtable on day two of the GSMA M360 EURASIA 2023 …

Pradeep Shilige, Chief Information Officer, Burjeel Holdings, has outlined how the private healthcare leader has leveraged the power of cloud technology to completely transform and enhance patient healthcare across the UAE, in the latest interview in our exclusive Mission Critical Master Series.
Mark Forker, spoke to K.S. Parag, FVC, and Nicolas Bliaux, Jabra, to discuss their recently announced distribution partnership and how this will change the landscape of intelligent video solutions going forward.

The Rise of Service Robots by Mohammed Aldousari, Regional Robotics Lead at Proven Robotics.

Cisco has accelerated their Full Stack observability strategy with a new customer digital experience monitoring solution following a bi-directional integration …

Veronica Martin spoke to Dr. Mohammed Al Shamsi, Head of Technical Support at Emirates Health Services, to find out how …

Almost all UAE companies believe artificial intelligence (AI) can help them weather current economic uncertainty, but access gaps between technical …
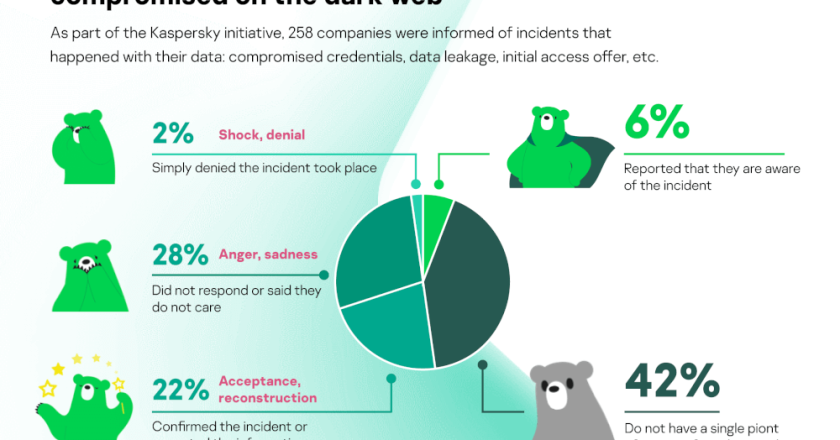
At the beginning of 2023 the share of users attacked with spyware in the Middle East increased by 11.8% from …

Veronica Martin caught up with Feras Zeidan, Regional Director META & South Asia at Mitel and Veer Passi, Group CEO …

Industrial control systems (ICS) are used to run modern critical infrastructure, including energy stations and nuclear power plants. These objects …

Kaspersky announced its training and Internship program in Saudi Arabia, further fueling its commitment to build national capabilities within the …

Kaspersky researchers announced the discovery of a series of attacks by a new malware supposedly developed by the infamous OilRig …

As the Treasury Automation helps treasury teams to harness more data and employ more analytics, those teams will become more strategic and capable of meeting their CFOs’ expectations.

Simran Bagga, Omnix, on how a people-first strategy has helped the company grow from strength to strength.