
Infoblox Threat Intel explores some of the trends it has been seeing leading up to the Paris 2024 Olympics.
Every iteration of the Olympic games is a major global event – fuelling pride and competition, watched by millions in homes around the world, and by thousands who travel to watch events in person. Such large audiences and levels of international interest have consequently drawn the attention of cybercriminals, some of whom have been preparing since before the Olympic national teams were even finalized. In this blog we will share some of the trends we have been seeing leading up to and following the opening of the Paris Olympics.
Sprinting Towards Fast Cash
Among the myriad phishing and spear phishing lures related to the games, ticket sale scams have been the most popular and common theme. Fraudulent ticket sale websites, mobile recharge plan offers, and merchandise seller scams have been widespread leading up to the 26 July opening ceremonies, but there have also been customised email campaigns to spear phish targeted audiences. A world of nefarious options for a global pool of victims. Moreover, according to a recent article from Fortinet, today’s phishing kits allow even the more inexperienced threat actors to get in on the action with a simple user interface to build out their campaigns.[i]
There have been hundreds of domains registered that allege to offer discounted tickets to the Paris Olympics. The landing pages to these websites are sophisticated, often user friendly, and appear so legitimate that almost anyone would have difficulty picking out the real page (tickets[.]paris2024[.]org), from the lookalikes, such as ticketsparis24[.]com. As shown by the images in Figure 1 below, even the landing page for this lookalike appears to lack many of the red flags often associated with fake sites, such as spelling errors, bad grammar and minimal content. Could you tell?
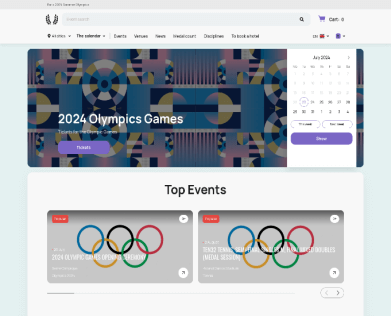
Identifying phishing pages like the one above is even more difficult when people are accustomed to being able to purchase tickets from legitimate sites that buy tickets in bulk and then resell them, such as StubHub and TicketMaster. If sports fans are not aware that the only legal way to sell or resell tickets to the Paris Olympics is to go through the site tickets[.]paris2024[.]org and use their platform, they are more likely to fall victim to well-designed fake sites.
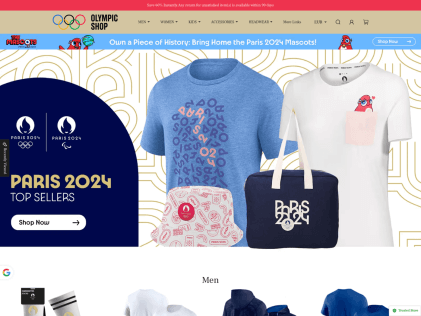
Threat actors are also spoofing merchandise websites and claiming to offer mobile data recharge plans. 2024olympics[.]shop and shop-olympics[.]shop are two domains claiming to sell merchandise, but in reality they steal the victims’ funds and information without ever sending any products. Like the ticket scam websites, the example in Figure 2 shows that the landing pages are well designed and do not show the characteristic red flags that often tip off casual users that they are phishing sites.

Going the Distance with Lookalikes
In 2023, Infoblox Threat Intel reported on the threat landscape of lookalike domains. These kinds of sites impact everyone – they pose challenges for security teams and are ever-present risks to individuals simply browsing the internet or scrolling through their email. It’s easy to see why nefarious actors favour them in their campaigns.
As an opportunity for cybercriminals, not only are the Olympic games globally popular and therefore offer a huge pool of potential victims, but they are recurring and predictable so the actors can prepare for them long in advance. Our lookalike detection algorithms picked up indicators that were created as early as September 2023 to spoof this summer’s games. Several examples include parissummerolympics2024[.]online, olympics2024[.]cc and olympicsparis[.]shop.
Just as Olympic athletes train for years to go for gold, we’re starting to see signs that threat actors are preparing for future opportunities. Based on the patterns we have seen from previous Olympic years, here are some examples of registered lookalike domains that we consider suspicious:
- parkcityolympics2034[.]com: The venue for the 2034 Winter Olympics in Salt Lake City, Utah, will be Park City Mountain.[i] This domain uses a self-named nameserver, a configuration that threat actors utilize regularly.
- 2028riversidecountyolympics[.]info: The equestrian events for the 2028 Summer Olympics in Las Angeles, California, will be held at a location in Riverside County.[ii] This domain is currently parked and is on a highly abused TLD.
- lakeperrisolympics2028[.]info: The rowing events for the 2028 Summer Olympics were initially scheduled to be held at Lake Perris State Recreation Area, but organisers have since determined that location to be too far from the main host city.[iii] This domain is also currently parked and is on a highly abused TLD.
Hacking Isn’t an Olympic Sport…Right?
Russia and Belarus were not invited to participate in the 2024 games; this has caused tensions to rise, particularly from hacktivists that support the two countries. These hacktivist groups, particularly those that support Russia, have gone as far as openly stating they would target the games on the dark web. Specifically, LulzSec, noname057(16), Cyber Army Russia Reborn, Cyber Dragon, and Dragonforce. Additionally, in March of this year, the French government admitted they had noticed unusually severe cyberattacks for which the group Anonymous Sudan has taken credit.[iv]
Past Olympic games have been targeted as well. In 2020, threat actors launched a cyber reconnaissance campaign against games officials in Tokyo, Japan. Russian groups launched the Olympic Destroyer Campaign at the 2018 winter games in PyeongChang, South Korea. The 2016 summer Olympics in Rio de Janeiro saw hack-and-leak attacks, and there were distributed denial of service (DDoS) attacks against the 2012 summer games in London.[v] Thus far we have only seen consumer-focused campaigns and some spear phishing for the current Olympics, but history shows that larger or even more targeted attacks are very possible.
The Finish Line
Analysing registrations and activity in the domain name system (DNS) has shown us that the “first heat” of cybercriminal activity related to the 2024 Olympic games have so far largely focused on phishing and scamming consumers looking for tickets, merchandise and necessities like mobile phone recharging plans. Fraudulent domains that are cleverly crafted lookalikes to legitimate sites put fans and followers at a high risk of financial loss and information theft. Some of the actors behind these scams have been preparing for months and aging their domains to avoid being blocked by security companies focusing on new indicators. We encourage participants and shoppers alike to avoid offers that appear too good to be true, to check beforehand the sites they plan to visit, and where possible, stick to official sites.
Indicators of Activity
A selection of indicators relating to nefarious Olympics-related activity is listed below and available in our Github repo .
| Indicators of Compromise | Type |
| ticketsparis24[.]com | Domain |
| 2024olympics[.]shop | Domain |
| shop-olympics[.]shop | Domain |
| parissummerolympics2024[.]online | Domain |
| olympics2024[.]cc | Domain |
| olympicsparis[.]shop | Domain |
| parkcityolympics2034[.]com | Domain |
| 2028riversidecountyolympics[.]info | Domain |
| lakeperrisolympics2028[.]info | Domain |
Infoblox Threat Intel
Infoblox Threat Intel is the leading creator of original DNS threat intelligence, distinguishing itself in a sea of aggregators. What sets us apart? Two things: mad DNS skills and unparalleled visibility. DNS is notoriously tricky to interpret and hunt from, but our deep understanding and unique access give us a backstage pass to the internet’s inner workings. We’re proactive, not just defensive, using our insights to disrupt cybercrime where it begins. We also believe in sharing knowledge to support the broader security community by publishing detailed research and releasing indicators on GitHub. In addition, our intel is seamlessly integrated into our Infoblox DNS Detection and Response solutions, so customers automatically get the benefits of it, along with ridiculously low false positive rates.
[i] https://www.parkrecord.com/news/winter-olympics-of-2034-awarded-to-utah-with-park-city-as-a-key-to-games/#:~:text=The%20International%20Olympic%20Committee%20on,and%20influence%20the%20trajectory%20of
[ii] https://www.dailynews.com/2024/07/19/with-venues-nearly-set-for-2028-la-olympics-cities-hope-for-cache-tourist-cash/
[iii] https://www.aljazeera.com/opinions/2021/12/21/olympics-2028-rowing-course-shortened-for-logistics-and-exposure
[iv] https://www.fortinet.com/blog/threat-research/dark-web-shows-cybercriminals-ready-for-olympics
[v] https://www.withsecure.com/content/dam/with-secure/en/resources-library/202407_WithSecure_Olympics_Threat_Report_ENG.pdf
Image Credit: Infoblox





