Huawei calls the Windows Phone platform weak despite using it as the foundation for some of the smartphones it makes.


Huawei calls the Windows Phone platform weak despite using it as the foundation for some of the smartphones it makes.
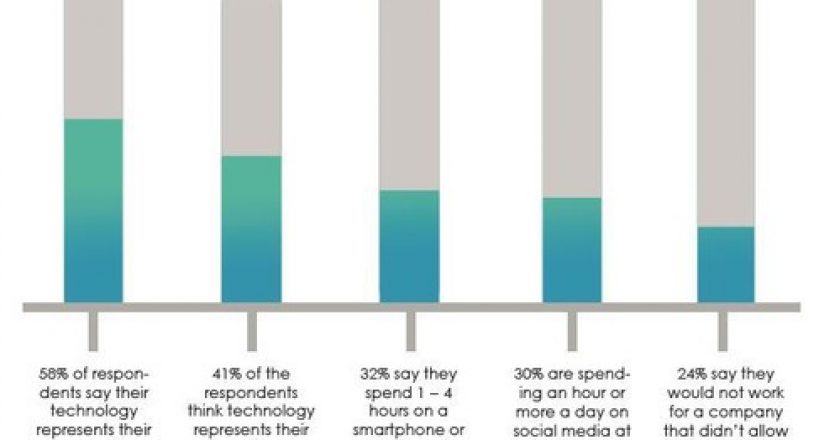
Technology has changed everything we know about the office. Now it is threatening to get rid of the office as we know it.

SAP has significantly improved the security of its products over the past few years but many of its customers are negligent with their deployments, which exposes them to potential attacks that could cripple their businesses, according to security researchers.

Despite the promise of portability from service providers, the reality of the cloud for big customers is a similar type …
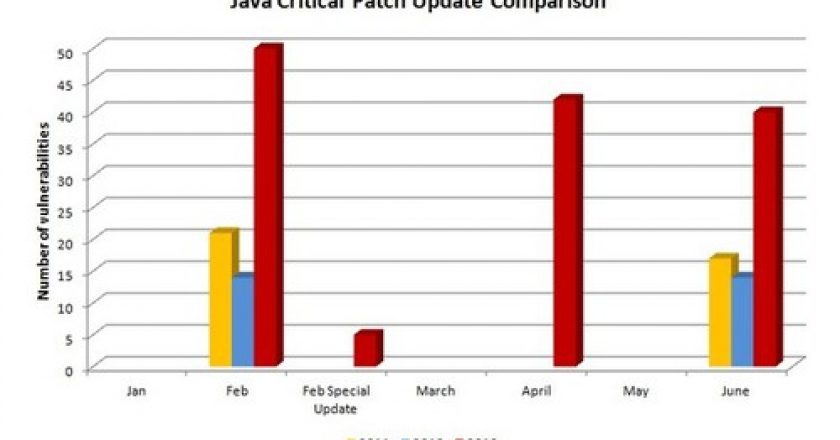
Oracle released a huge update for the virtually ubiquitous software, but attackers aren’t done exploiting Java as the weakest link in the security chain, and Oracle isn’t securing it fast enough.

A recent study of small- and medium-sized businesses in the US and Europe revealed that many of them are facing challenges in implementing back-up and recovery solutions that can help protect their businesses.

Carl Icahn has acquired a larger stake in Dell and called for a better buy-out offer than the proposal of US$13.65 per share from Michael Dell and Silver Lake Partners.

The source code for the Carberp banking Trojan program is being offered for sale on the underground market at a very affordable price.

The average organisation believes it would spot a data breach in 10 hours, a McAfee global survey of IT professionals has found. But is that result good, indifferent or an indication of the downright complacent?

Wall Street plans to hold a simulated cyber-attack against equity markets this month that experts hope will set an example of how industries should test their defences against assailants.

Lean storage techniques will keep a lid on storage investments over the next few years, though the world’s enterprises still are on track to buy 138 exabytes of storage system capacity in 2017, IDC said.

More than 30 computer scientists signed off on a court brief opposing Oracle’s effort to copyright its Java APIs, a move they say would hold back the computer industry and make technology more expensive.

Hackers have found a devious new way to disseminate malware: They’re using peer-to-peer networks.

Revelations over the U.S. National Security Agency’s Prism surveillance programme have much of the general public in uproar, but in terms of the controversy’s impact to enterprise IT, some CIOs have measured, albeit watchful reactions.